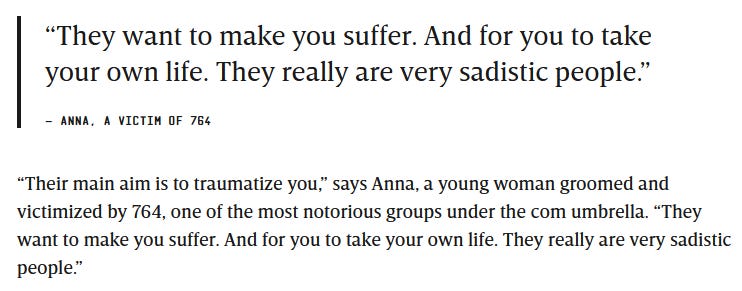OSINT Insider Issue #4 - RIP Skype, How/Why We Should Preserve OSINT Data from Online Platforms
Skype is not the first, and it certainly won’t be the last social platform to vanish. But it may be one of the largest to disappear without a trace—and that should scare all of us.
In the early 2000s, Skype was a revolution. Peer-to-peer encrypted calling, decentralized infrastructure, and global accessibility made it the backbone of online communication. It was used by journalists, cybercriminals, scam rings, professionals, gamers, teenage friends, online predators; you name it. And now, it’s vanishing.
Microsoft made it clear with their recent notice, Skype is being phased out in favor of Teams. Services are sunsetting next month. Old user profiles will no longer be searchable; only the users who logged in and agreed to transfer to Microsoft Teams will be searchable on Microsoft Teams. The metadata that caused my parents to tell me “the internet is forever” is vanishing. And unless we act fast, we’ll lose a piece of digital history—and vital links in countless investigations.
The Consequences of Disappearing Data
The loss of a platform like Skype is more than inconvenient. It’s catastrophic for open-source intelligence (OSINT) and for survivors of digital crimes. I want to explain why. This one is personal.
When I was 14, I was manipulated on Skype. Groomed by a predator, coerced into performing acts on camera that I didn’t understand. Once I had fully grasped what happened to me later on in life, I was left feeling ashamed, scared, and violated, with little to no recourse. It was this experience that ultimately led me down a path into the OSINT world, in hopes I could use this technology to catch these horrible people and save kids from what had happened to me. But my abusers knew what they were doing; how to stay anonymous and how to disappear. They used Skype because it was easy for a child to set up/use, and because it gave them instant access to vulnerable kids.
This sort of grooming was and is still done on many millions of kids, and the material produced by it, known as self-generated CSAM (Child Sexual Abuse Material), is usually sold to pedophiles through the dark web. Essentially, online video calling platforms like Skype, and in more recent times, Discord, are used to systematically produce CSAM from children all around the world and then sell it. It is a form of digitally assisted human trafficking done at scale.
In recent years, the problem of self-generated CSAM has become more apparent, with sadistic groups like 764 receiving mainstream attention for their exploitation of vulnerable children. Groups like 764 don’t just stop at self-generated CSAM; they groom and then extort children into producing much more sadistic material, such as self-mutilation/self-harm, bestiality/animal abuse (including against minors’ own pets), and in extreme cases, imagery of the child taking their own life. I got lucky, it could have been so much worse.
I’ve spent the last half a decade trying to make sense of what happened to me. Digging. Tracing usernames. Following aliases through breached data and old forum posts. But the only digital thread connecting back to them—their Skype handle—is going dark. And once it’s gone, so is any chance I have of proving what happened to me and that the handle ever existed at all. That’s not just a personal tragedy. That’s an investigative dead-end in a case that could still be cracked.
And I know I’m not alone. Skype was one of the most commonly used platforms for CSAM producers during the early and mid-2010s. They exploited Skype’s pervasiveness and ease of use, leveraged its video calling tools, and preyed on vulnerable kids across the world, many of whom were tricked into self-producing material that would haunt them for years. We’re not talking dozens of victims. We’re talking thousands. Maybe hundreds of thousands. And every lost profile, every unreachable handle, is vital evidence lost in a case that still matters.
But this affects more than just CSAM production and grooming victims, it affects many different crime sets:
Case Study 1: Cryptocurrency Scam Ring
Imagine a fraud group that ran investment scams from 2010 to 2012. Victims were lured into sketchy schemes via Facebook. But communication? That happened over Skype.
The scammers used unique usernames tied to fake trading firms. Years later, victims start reporting the fraud, but the money trail is cold. The Skype group was deleted, evidence wiped, and any recollection of the fraudsters’ Skype username is gone. The only shared clue? A comment buried deep under a YouTube video:
“If you are really interested in investing, you should message me on Skype: StantonCapitalOfficial
However, they don’t know if this is the same Skype alias they communicated with all of those years ago or not, and this happened so long ago that none of them have their old Skype accounts anymore (nor will any of them be able to search the messages of their old accounts after Skype shuts down)
If that alias still exists, even without access to their accounts, the data on their Skype profile sharing the same username can be found and then used to cross-reference with what they already know to confirm it’s them. From there, they can report the crime to authorities and just maybe find justice.
But if it’s gone? There’s no way to even begin that work, no way to prove this profile ever existed.
Case Study 2: Ransomware Operator Trail
Imagine a well-known ransomware group used Skype for initial outreach to victims back in the early 2010s. Payment negotiations, extortion threats, and tech support all funneled through a small group of public-facing aliases.
Flash forward a decade. That group is inactive, but some of its infrastructure becomes relevant again. A new malware variant uses old code and domains tied to the once thought to be inactive group. An email address shows up in a new campaign. The only consistent datapoint across the two groups? A Skype name last seen in 2014 is linked to both of their emails.
If that data had been preserved, it could be used to link campaigns. But when Microsoft wipes that profile, the connection dies with it.
This Effects All of OSINT
In the OSINT (Open Source Intelligence) world, platforms like OSINT Industries, Epieos, and lolarchiver offer a critical service: starting with something as small as an email address, investigators can build a surprisingly comprehensive map of a person's digital footprint—from what services they’ve signed up for, to usernames they use across platforms, even hints about where they might live.
But that map is shrinking, and every time a platform like Skype shuts down, it gets even smaller.
A Race Against Time and Platform Lockdowns
Many of these tools rely on public or semi-public data leaks, API quirks, unintended usage of features, or publicly accessible user directories. And over time, platforms catch on. They patch those holes. They lock things down. They stop returning data. And each time that happens, a piece of the digital investigation puzzle becomes permanently obscured.
An example of this happening can be found with GHUNT, a popular OSINT tool that allows you to retrieve information from Google using an email address.
Over the years, the developer of GHUNT has had to update the app multiple times as Google has slowly restricted what data can be accessed and killed certain products that used to provide data. Older versions of GHUNT used to be able to retrieve photos from public Google Photo Albums and Picasa (a now-dead Google product). They’ve also had to update it after Google restricted what information is available via Google Maps reviewer profiles.
Skype is no exception. OSINT platforms currently allow you to find someone’s Skype profile and the information within by searching for their username OR the email address/phone number connected to their account.
But soon? These platforms won’t return results for Skype. And platforms like OSINT Industries, Epieos, etc don’t archive results, so once the Skype platform is shut down, all of that data becomes dust to anyone who searches after the shutdown. No trail. No context. No evidence.
So, what’s the solution?
Here’s the playbook: Using automation (and evasion tactics like residential proxies), you systematically query platforms like Skype to find which selectors are still live. Once a profile is identified, the relevant metadata is scraped and stored: creation date, bio, associated names, country flags, friend lists, last seen timestamps, etc. Anything that might become useful later, even if it doesn't seem critical now.
But it’s not as easy as it sounds.
The roadblocks are many: aggressive rate-limiting, anti-bot systems, the costs of using residential or mobile proxies at scale, and—of course—the legal and ethical quicksand of scraping platforms that explicitly prohibit it in their terms of service.
The Technical Challenge of Saving a Platform’s Data
Preserving OSINT data isn’t as easy as hitting “download.” Especially for social/communication platforms like Skype, we face four major barriers:
Rate limits and bot detection
Querying millions of profiles is expensive. Rotating residential proxies, mobile proxies, captcha solvers, headless browsers; these things all cost money and require infrastructure. And as platforms grow more hostile to scrapers due to the rise of AI and the need for training data, these challenges multiply.Archival decay and takedown requests
Even if you collect the data, storing it over time is a separate war. Archive.org, our most reliable friend, is stretched thin and underfunded. GitHub is great, but it isn’t built for long-term preservation of high-volume OSINT dumps. And once a dataset gets flagged or a court order is received? Gone.Ethical and legal grey areas
Many platforms’ Terms of Service explicitly forbid scraping, archiving, or redistributing profile data. Even if the intent is preservation or investigation, this can violate local laws, especially in privacy-heavy jurisdictions like the EU.Incomplete Coverage
We can’t expect to scrape every possible username; the total number of queries required would easily exceed trillions by the time we got to usernames eight characters or longer (More than 3,025,989,069,143,040 usernames to be exact)
Solutions (or at Least Ideas)
So, how do we fix this, or at least buy ourselves more time?
Targeted scraping:
Instead of trying to crawl every username possible, we can start with known selectors—emails and usernames exposed in data breaches or existing investigative datasets. These can be run against platforms like Skype to build partial but useful archives of profiles.Distributed storage/internet:
Instead of uploading everything to one site, we can build mirrored repositories across centralized and decentralized platforms like GitHub, GitLab, archive.org, IPFS, BitTorrent, etc.Crowdsourced proxying:
An idea inspired by BOINC, the distributed computing platform used for science, we could develop a network of volunteers who donate bandwidth for data preservation. A sort of slow, ethical residential proxy powered by community nodes. Yes, this flirts dangerously close to DDoS mechanics if misused, but with proper throttling, coordination, and respect, it could be done.
How OSINT Platforms Could Help
Platforms like OSINT Industries are fantastic, but they don’t save results. And they operate in the UK, meaning their privacy compliance restricts what they could legally preserve anyway.
The same is true for many other OSINT platforms, focused on scraping, searching, link analysis, and analytics. But no one is building an Archive.org for digital footprints. If these platforms could start archiving results from their tools and making them available, it could provide another historical archive of someone’s digital footprint. But even then, we need a coordinated effort with extensive coverage, not just one platform keeping track of what’s already being searched.
We’ve Done It Before — We Can Do It Again
Skype isn’t the first platform on the brink, and it won’t be the last. But we’ve seen how preservation can work; if there’s enough community willpower behind it.
Neocities: A Digital Time Capsule That Fights Back
Neocities is a spiritual successor to GeoCities. When Yahoo shut down GeoCities in 2009, nearly 38 million web pages were erased in one swoop. But volunteers jumped in. The Archive Team, an internet preservation collective, managed to scrape and preserve about 1TB of content before the plug was pulled. That archive still lives today as a browsable piece of internet history.




Neocities learned from that collapse. It encourages preservation by default. Pages are static, easily mirrored, and community-driven. In many ways, it’s the opposite of today’s walled gardens.
Google+ and the Archive Team’s Race Against the Clock
When Google+ shut down in 2019, the writing was on the wall for months. But despite the advance warning, Google didn’t offer a clean export for public pages or communities. Enter the Archive Team again. Using custom scrapers and volunteer-run infrastructure, they salvaged over 1.5 million public posts, which are still accessible through the Internet Archive.
Was it perfect? No. Private messages, niche communities, and images hosted externally were lost. But the larger lesson holds: with a distributed team and some coordination, we can preserve huge slices of the internet, even when platforms don’t want us to.
Time is Running Out
Skype shuts down on May 5, 2025. The old Skype user database will disappear completely in January 2026, with neither Skype nor anyone else possessing it. Then maybe Telegram purges inactive handles. Then, major platforms start patching the ways we collect data about people’s digital footprint. The dominoes can fall quickly.
Every time a platform dies, we lose clues. We lose evidence. And we lose the chance to bring closure to people like me, who still live with unanswered questions from when we were 14.
I may never find the people who hurt me. But I’m not ready to give up that chance for others. And I know thousands of OSINTers feel the same. We likely don’t have enough time to scrape Skype, but let the loss of this data be a lesson; we need to solve the overarching problem.
If we want truth, justice, and accountability in a world where more and more crime is digital, then OSINT data is sacred—and it must be preserved.
For my paid subscribers:
I believe this article is important to the wider industry and educates readers on a variety of relevant topics; however, I recognize that my paid subscribers may feel differently. I want to ensure those who are supporting me monetarily feel they are getting value out of my content. For that reason, I have prepared this sneak peek of our upcoming issue on tools for network-related lookups, including tools that aggregate domain, IP, certificate, cookie, and device information across the global internet for lookups: