OSINT Insider Issue #6 - OSINT Tool Breaks Federal Law?
There are many data sources that can be invaluable when investigating people, but some pose hidden risks such as non-compliant data sources that may risk burning cases when they arrive too court.
There are many OSINT data sources and tools that can be invaluable when performing investigations, but some data sources are restricted to certain professionals, such as licensed private investigators. This is because these data sources provide legally protected data, such as credit header data. Today, we are going to talk about data sources like these, a rogue OSINT tool illegally selling it, and the risks associated with it.
This edition will cover:
New OSINT Tools/News
Fascinating List of Threat Actor Datasets
Tool to Analyze Push Tokens
New OSINT Tool, Find Location of Screenshot Using The Weather
Tool for Monitoring GPS Jamming Globally
Tool for Finding the True Owner of NYC Property
Massive New Reddit Database (More than 3.6 TB!)
New Instagram Map Feature, OSINT Goldmine?
FaceSeek, New Facial Recognition Platform
Tool for Finding Instagram Posts from Private Profiles
New OSINT Tool Has Unique Discord Username History Feature and Discord IP Address Data
Free Alternative to Forensic OSINT, A Tool for Forensic Evidence Collection
New Tool, Ship Wreck Tracker
New Tool, Mega.nz File Search Engine
and more
Laws Protecting Certain Kinds of Data
Explanation of Credit Header Data
An OSINT Tool Breaking Federal Law?
Previous Edition/New Special Edition:
In this special edition of the OSINT Insider, we dived deep into the connections and activities involving North Korean Universities and the rest of the world. From uncovering knowledge sharing deals between North Korean and Russian/Chinese universities to analyzing satellite imagery of North Korea’s expanding university campuses. Read more here.
OSINT News/New Tools:
Starting with this edition, each newsletter will now come with a digest of relevant news, tools, etc, for OSINT practitioners, increasing the overall value of the newsletter for readers.
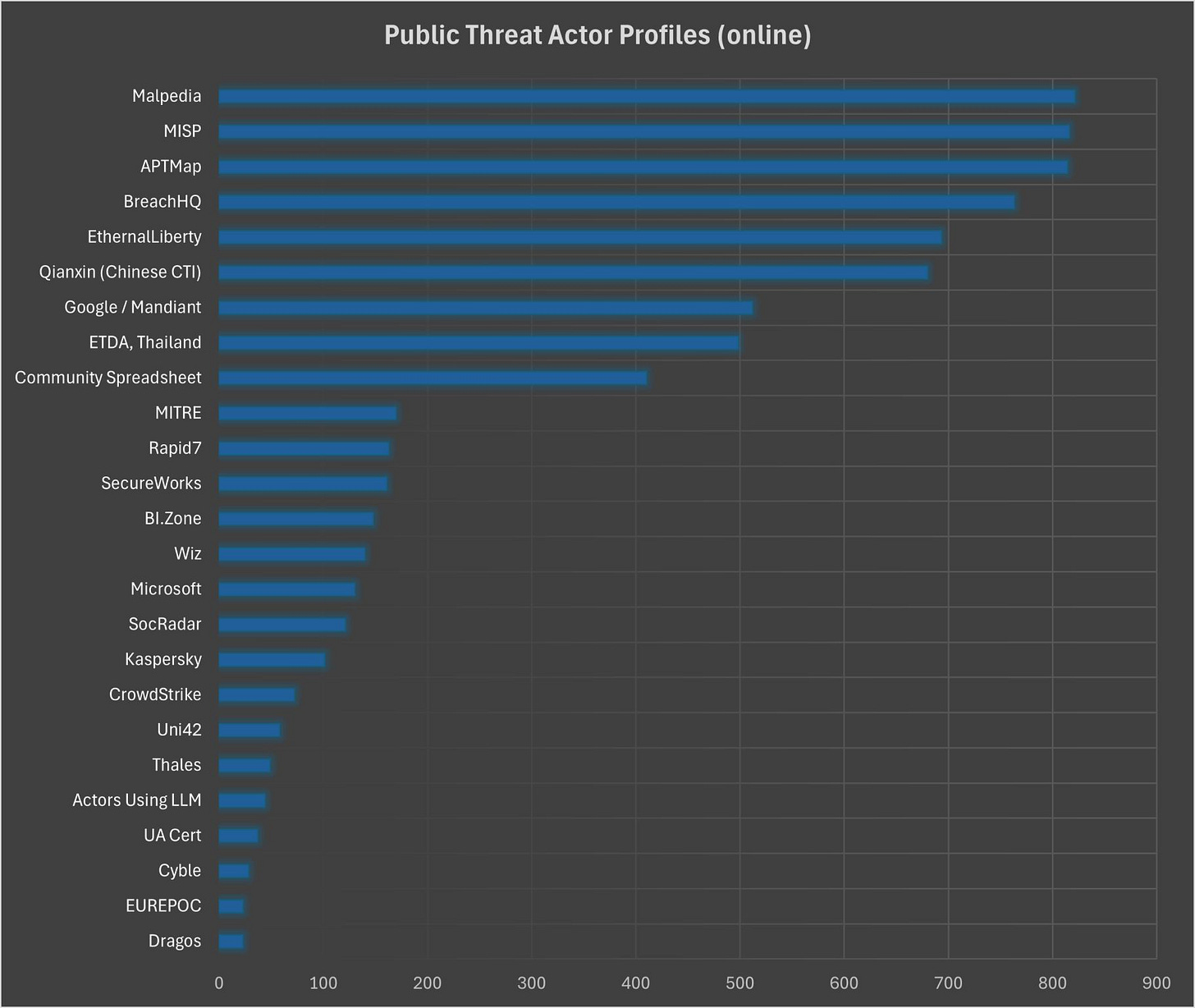
📌 Fascinating List of Threat Actor Datasets by Yury Sergeev
Yury analyzed how many unique threat actor profiles each data source on the list has.
https://www.linkedin.com/feed/update/urn:li:activity:7332993229232971776/
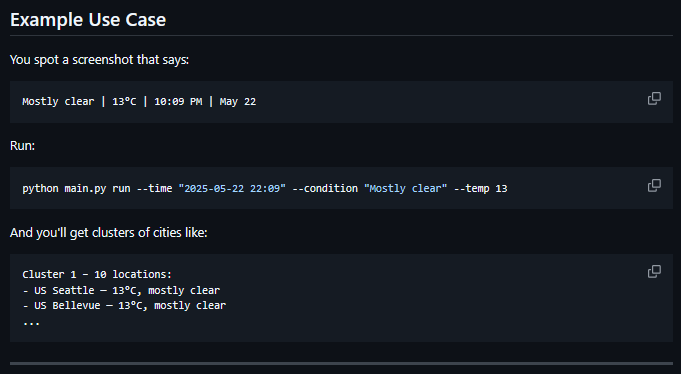
📌 New OSINT Tool, Weather2Geo
People post screenshots with the Windows weather widget in their taskbar all the time, showing the exact temperature, weather condition, and local time. This tool uses the same API as the widget to find cities where those conditions are currently true.
https://github.com/elliott-diy/Weather2Geo
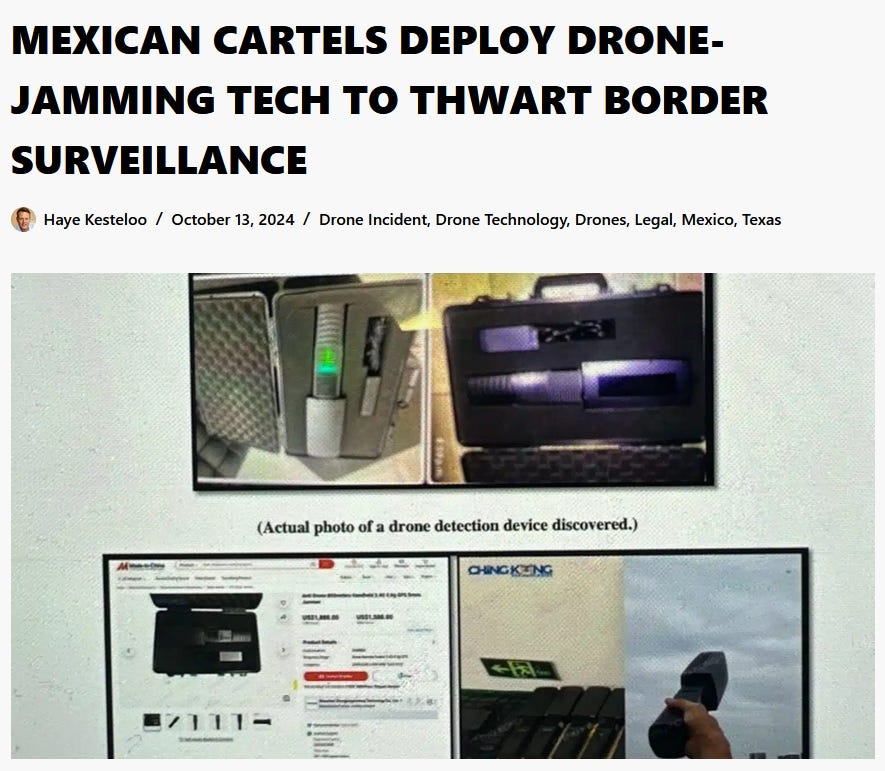
📌 Tool For Monitoring GPS Jamming Around the World
Recent activity on the US-Mexico border with GPS jamming brought this tool into the spotlight once again. It was used to monitor the use of GPS jamming tech by cartels in an OSINT Discord server recently. Here’s an unrelated article on the subject of GPS jamming by cartels if you’d like to learn more: https://dronexl.co/2024/10/13/mexican-cartels-drone-jamming-border-surveillance/
📌 Tool for Identifying Property Owners in NYC
A new tool, by the JustFix project, aims to help tenants in NYC identify their landlords based on ownership information. Can search by name or legal entity, which can be helpful with identifying portfolios of properties, hidden under shell structures.
https://whoownswhat.justfix.org/en/
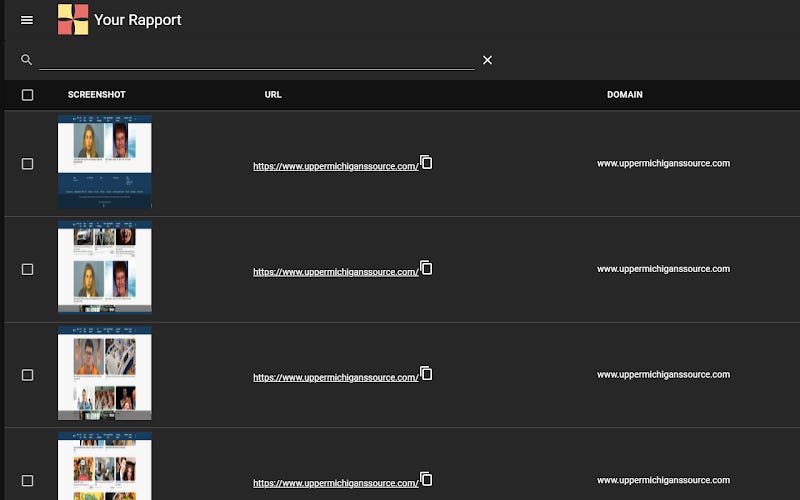
📌 Free Alternative to Forensic OSINT, A Tool for Forensic Evidence Collection
Free alternative to paid tools like Forensic OSINT has the following important features:
Signed Hash for verifying each screenshot's integrity
Multiple timestamps are collected
Multiple attributes about the computer that took the screenshot are captured
Source code is Open Source
https://github.com/yooper/your-rapport
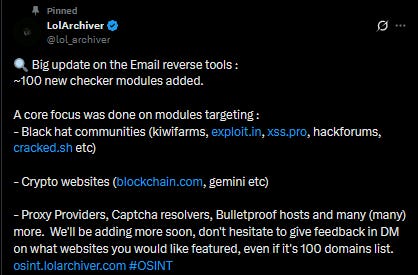
📌 LolArchiver Significantly Expands Module Support
lolarchiver, an emerging top competitor to tools like OSINT Industries and Epieos, has recently added support for an additional 100+ sites, including infrequently supported sites like KiwiFarms, Exploit.in, etc. They also expressed plans to add username search support for over 400 sites over the next couple of months!
https://x.com/lol_archiver/status/1956460179953766714
Advertisement/Promotion
infostealers.info
🔗 URL: https://infostealers.info/invite/712CAE1F
🛡️ Defanged: [https://infostealers[.]info/invite/712CAE1F]
Summary: Infostealer data is the new breach data, with billions of records publicly accessible online; it’s nonsensical not to make use of this powerful new OSINT data source.
And unlike breach data, which only reveals a single record from a single company, infostealer data is a subject’s entire digital footprint. Every website they saved a password to, the URL of every website that stored a cookie on their device (yes, even those ones), the names of their files and folders, their saved payment methods, and autofill data, it’s a treasure trove for digital investigators.
When you get a hit, the case is over; you have everything you need. Use it to identify users of CSAM distribution websites or cybercrime forums, use it to make an incredible leads list of your competitor’s product, make it your skiptracing or phone append super power, the potential is truly unlimited with this new datasource. Sign up for infostealers.info today and get 3 free demo searches!Data Available:
Saved passwords and logins from the browsers of over 50 million devices around the world (also contains the URL the password was saved to, providing a powerful digital footprint), over 20 billion records in total
Autofill data (Can include information like full name, billing addresses, shipping addresses, contact information, or anything else someone might save to their browser)
Search By:
Phone Number
Email Address
Username
Domain
Password
Any Keyword - Name, Address, etc (Mostly restricted to autofill data searches)
COMP ID (Gets all of the data from a specific device)
Cost: $1 per credit
Non-pro accounts will have a censored password field everywhere to prevent misuse of data; the URL field remains uncensored everywhere, and the login field is only very partially censored in domain search results to prevent misuse.
$200 per year for Pro access (requires KYC) to get all results, including the censored results.
Other Important Details:
The full password and autofill field values are censored for users who have not successfully undergone KYC. Only the URL and Login field are visible for non-KYCed users in order to prevent misuse of the data.
It’s recommended to use infostealer data as a starting point and then perform parallel reconstruction efforts, as this data may not be admissible in court under the fruit of the poison tree doctrine.
The full platform provides additional data from infostealer logs in search results, such as stored cookies (acts as a pseudo browsing history), autofill data (can include addresses), saved payment methods (credit cards), and system information (file tree). You can also export the raw contents of the logs, which contains information vital for incident response (exact time of infection, device hostname, IP address, directory of infection, etc), and even more data like actual browsing history, desktop screenshots, installed programs, cryptowallet information, and more. And you can search using more advanced search features, including keyword searches (with boolean and wildcard support), searches against URLs, credit card numbers, file/folder name search, and more! Learn more about the full platform here, and reach out for a trial: https://www.farnsworthintelligence.com/infostealer-data
Sign up to get 3 free demo search credits to test out the product!
Law enforcement working in ICAC units can reach out for free access at: lea@farnsworthintelligence.com
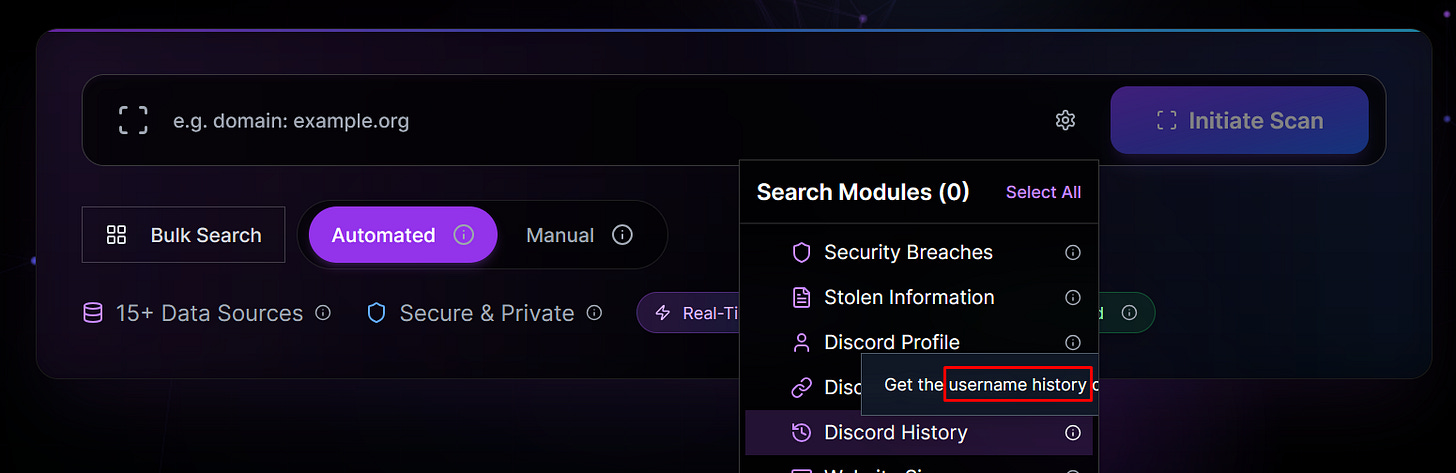
📌 New OSINT Tool Has Unique Discord Username History Feature and Discord IP Address Data
WARNING: This tool may be connected to a loose network of potentially criminal OSINT tools; use at your own risk.
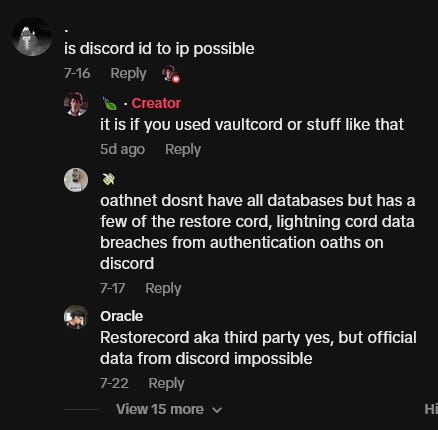
Oathnet, a new OSINT tool, comes onto the scene with features commonly seen elsewhere in the industry, but with a unique Discord username history module. The tool is already down as of the last revision to this section (8/21/2025).
At least some of the Discord data for this tool is likely sourced from previous breaches or authorized resale of data from 3rd-party Discord bots, such as VaultCord, LightningCord, RestoreCord, etc. Speculations in TikTok videos featuring the tool agree:
📌 BigBang, A Better Lightweight Alternative to Free Tools from HuntIntel
Find content based on location, from Google, Instagram, Facebook, and Twitter. Similar to the freemium tools offered by HuntIntel, such as InstaHunt, but with no rate limits.
https://www.majdkhalifeh.com/bigbang
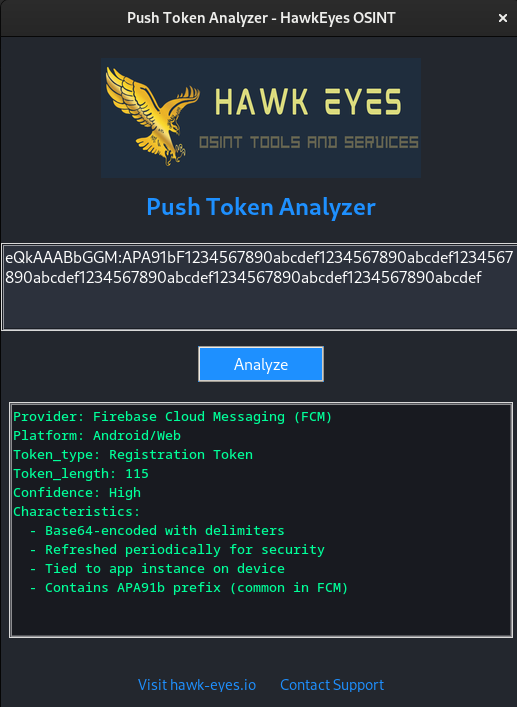
📌 New Tool for Analyzing Push Tokens
Push tokens are unique identifiers assigned to mobile devices by notification services (Apple APNs, Google FCM). In OSINT investigations, these tokens can be found in leaked databases, app logs, or through device forensics. Analyzing push tokens can help link devices to specific users, identify the type of device, or correlate activity across multiple platforms.
https://github.com/HawkEyes-OSINT/PushToken_Analysis
📌 New Facial Recognition Tool, FaceSeek, Misleading Claims from Reddit (Again), A Little Less Shadyness
FaceSeek has recently come onto the scene as a competitor to tools like FaceCheck.
While some Redditors have claimed it is simply reselling FaceCheck results, we ran searches against it using faces that have been removed from FaceCheck results. These removed results still appeared on FaceSeek, which would be impossible if they simply resold results from FaceCheck. This test is important because having the same results from two tools does not always mean they are stealing from one another; it could just be that their coverage is very similar. This test, however, does not preclude the possibility that FaceSeek has stolen FaceCheck’s private database of scraped faces + source URLs, or any other possible explanation.
The company appears to be located in the same location as the offices of FaceOnLive (according to the address in their footer), a seemingly legitimate and potentially affiliated company in Canada with a legal business registration and a large online footprint. Their business records also openly disclose their directors (Jesse Zhang and Volodymyr Hrynkevych). However, this company was recently dissolved for noncompliance by the Canadian government (https://ised-isde.canada.ca/cc/lgcy/fdrlCrpDtls.html?corpId=14556313)
Jesse Zhang shares the name of a few different AI/ML experts and other technical experts, making it unclear which real Jesse Zhang actaully started this company (if any). The location of their office appears to be a registered agent, with many other businesses operating out of the same location. This is, at least, a little less shady than the mysterious origins of FaceCheck.id, whose offices are located in Belize, in the same location as other shady businesses included in the Panama Papers (https://offshoreleaks.icij.org/nodes/14085279)
Discovering who is really behind FaceOnLive does seem doable, and we would encourage other researchers to look into this.
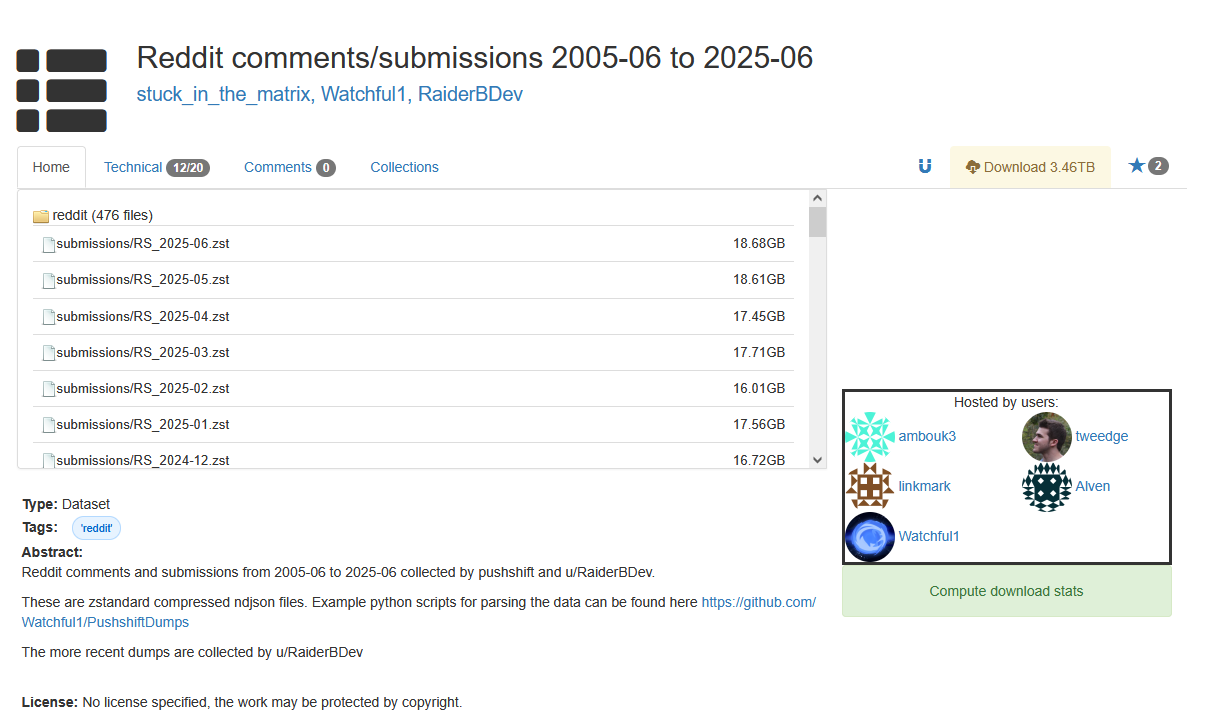
📌 Massive New Reddit Dataset, Scrape of 99% of Reddit, 3.46 TB in size!
The developers behind Pushshift recently released what is likely the largest scrape of Reddit so far. They claim to have scrapped 99% of the site, and the data is freely available. The dataset includes the content and author, making it highly useful for OSINT purposes. The data is 3.46 TB in total size, but consists of smaller chunks (~20 GB each) separated by date range.
https://academictorrents.com/details/30dee5f0406da7a353aff6a8caa2d54fd01f2ca1
📌 New Instagram Tool Pulls Posts from Private Profiles
This script allows you to pull any posts a private Instagram profile was tagged in via the Instagram API. It does this using a hardcoded app ID; however, this app ID belongs to an internal Instagram service and is unlikely to be changed (You can find the app ID it uses in here: https://www.instagram.com/static/bundles/es6/ConsumerLibCommons.js/faada8fcb55f.js) This isn’t the first such script to pull this off (others using the same app ID are findable on Github), however it seems to be the first to focus on private Instagram profile data and linked posts.
https://github.com/obitouka/InstagramPrivSniffer
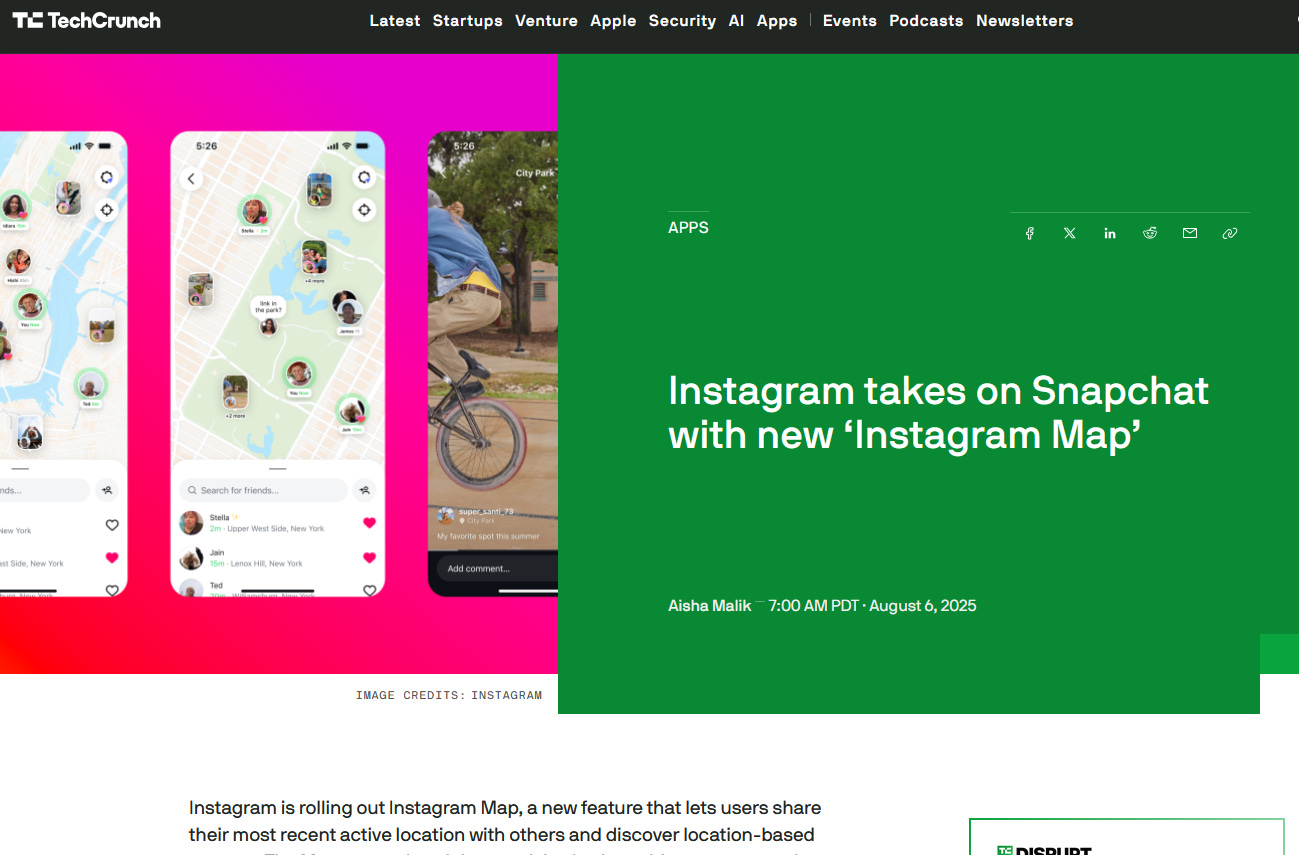
📌 New Instagram Map Feature, SnapMaps Goldmine 2.0?
SnapMaps was a boon for OSINT (Link goes to an OSINT tool for the now-defunct public SnapMap webpage - SnapMaps is only accessible via the Snapchat app now). Could this new Instagram map feature be the same? It’s only a matter of time until tool developers make it apparent just how useful this feature could be for OSINT.
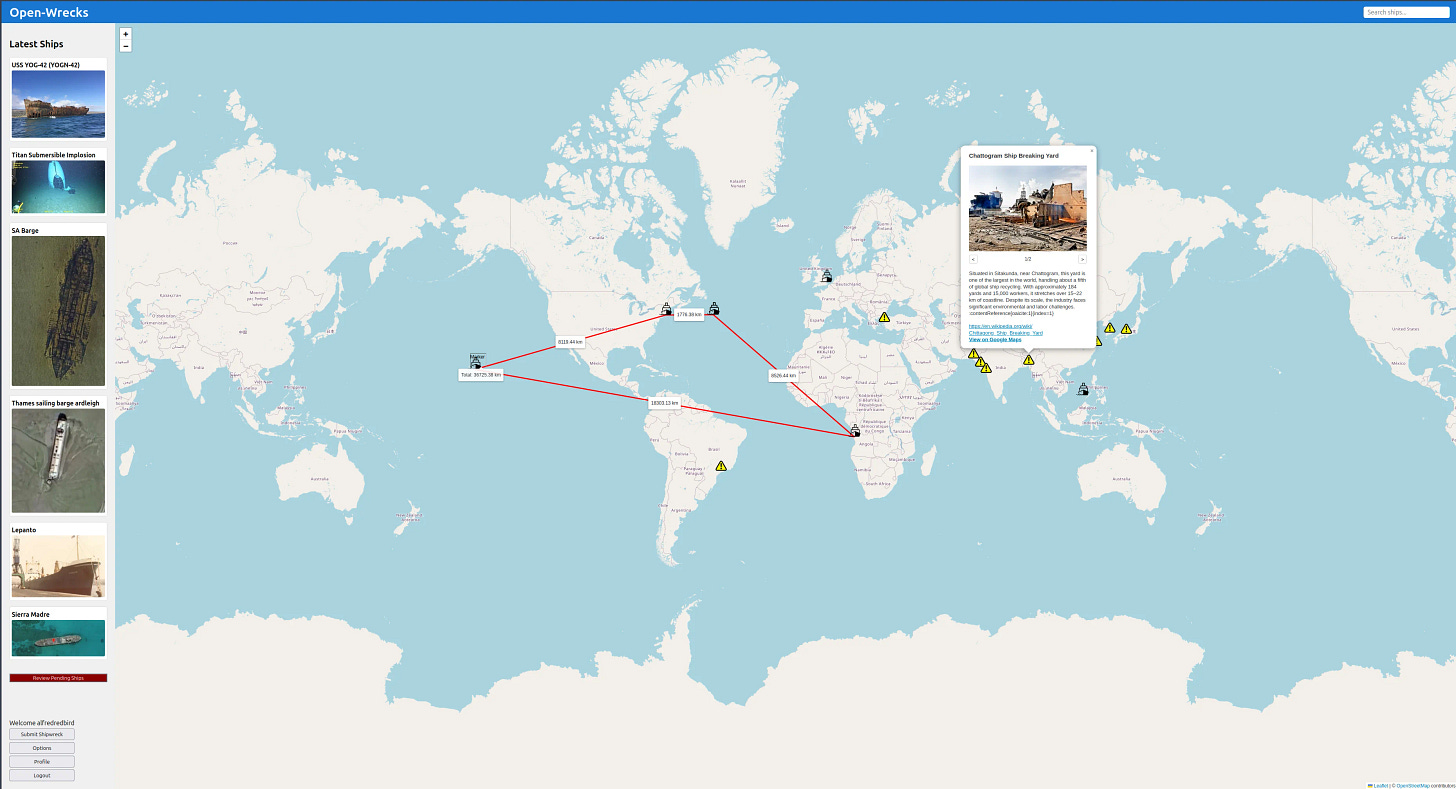
📌 New Tool, Ship Wreck Tracker
A new tool that catalogues and maps detailed information about ship wrecks, including how they sank, IMO’s, the location, ship owners, etc.
https://github.com/Alfredredbird/Open-Wrecks
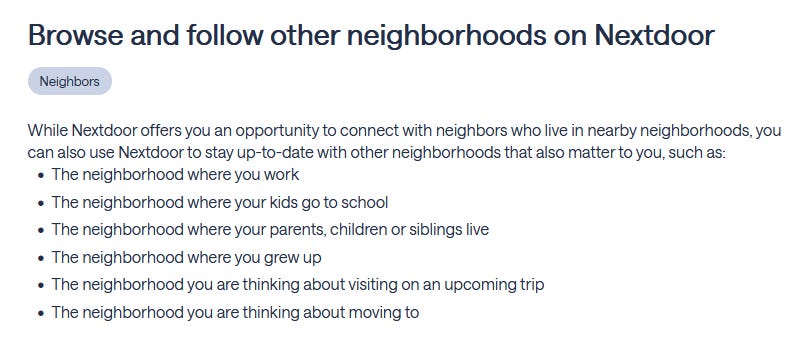
📌 OSINT Tip: Accessing Any Neighborhood on Nextdoor
A new post by Steven Mason features an overlooked tactic for finding unknown witnesses or gathering hyperlocal intelligence: using Nextdoor (the app)
While many assume you're limited to your neighborhood, Mason explains that you can access posts from other areas, a game-changer for proximity-based investigations.
Profiles often include full names, and the platform’s casual tone leads to open discussions that can surface leads, verify timelines, or confirm who was active in a particular area. Mason credits this method with reviving dead cases and deepening client relationships.
https://www.linkedin.com/feed/update/urn:li:activity:7349190602447626242/
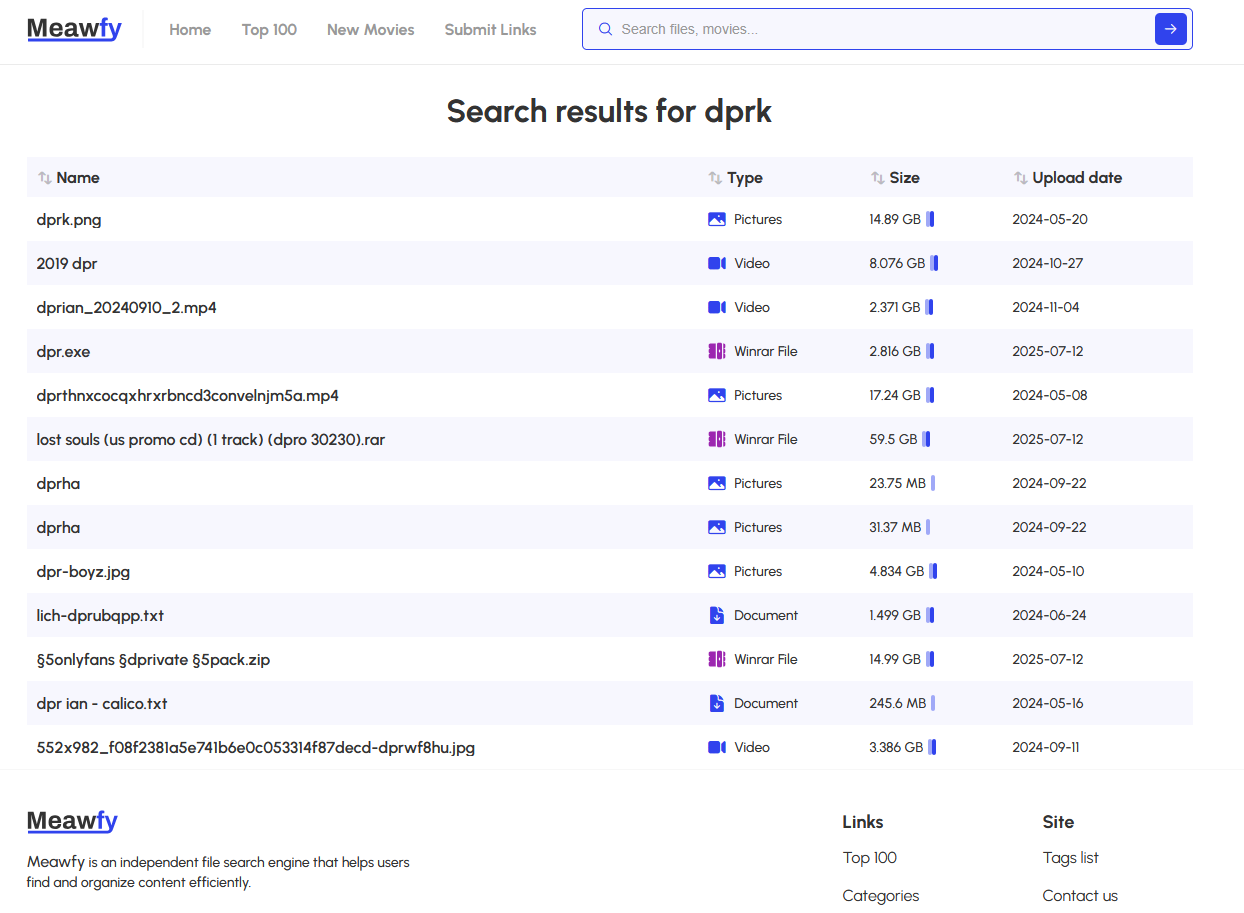
📌 New Tool, Mega.nz File Search Engine
A new search engine for finding unlisted files hosted on Mega.nz! Claims to have indexed over 9 million files. Search by file name or browse categories. 🎩 H/T: Jake Creps, The OSINT Newsletter
https://meawfy.com/
If you appreciated how much value we put into this free OSINT digest section, please support us with a paid subscription:
OSINT Internship Opportunities
More than half of all interns at Farnsworth Intelligence have now been able to work on real cases by participating in our Junior Analyst program, accessible to all interns regardless of whether they are helping with the knowledge base project or a part of the content/product development internship program. Here’s what one of them had to say about the experience:
”Amazing! Thank you so much for letting us work on this. I learned so much that I would never be able to on my own, and really enjoyed the process! Honestly, all of this was new for me; I’m really at the beginning of my OSINT journey. My experience with OSINT up until this point has been a lot of reading and some Sofia Santos/Bellingcat challenges, so this put together a lot that I read about and exposed me to new tools and analysis.”
We still have many openings for our Content and Product Development Internship, so if you know anyone in the marketing, communications, copywriting, or adjacent fields, we would encourage you to share this exciting opportunity with them: https://www.farnsworthintelligence.com/opportunities#cntproductdevinternship (Direct Link to Internship Listing)
We also just launched a Junior Developer Internship, perfect for anyone looking to gain real development experience for their resume, so if you know anyone in the software development or computer science fields, we would encourage you to share this exciting opportunity with them: https://www.farnsworthintelligence.com/opportunities#jnrdevinternship (Direct Link to Internship Listing)
Find out about our other internship opportunities here: https://www.farnsworthintelligence.com/opportunities
Today’s Post - OSINT Tool Breaks Federal Law?:
Today’s post is going to focus on a specific OSINT tool that is potentially breaking US federal law, but before we can get to the tool, we are going to provide background information on the laws affecting certain kinds of data. Additionally, after we talk about the tool, we will provide information about how we determined it may be breaking a federal law.
Everything we claim in this edition is alleged; we are not lawyers, this is not legal advice, nor are they absolute claims. These are the conclusions we reached based on our expert understanding of the data ecosystem, but for legal reasons, it’s still alleged, and we can’t be 100% certain we are correct.
Want to see the rest of this post? You’ll need to become a paid subscriber first: