OSINT Insider Issue #7 - Exploring The World of Illegal/Underground OSINT
In this Halloween special of the OSINT Insider, we will be exploring a very, very spooky part of the OSINT world, the underground/illegal side of it! We'll showcase terrifyingly tools used to kill!?
In this Halloween special of the OSINT Insider, we will be exploring a very, very spooky part of the OSINT world, the underground/illegal side of it!
This edition will also cover:
New Dating App Lookup Tool, Powerful Resource for Private Investigators, Could Aid in Pedophile Sting Operations, Infidelity Investigations
Doogle.gg - A Ridiculously Powerful OSINT Tool for Discord, Could Be Used to Solve Cold Cases
Massive Venmo Transaction Scrape, Downloadable and Searchable Database
WACZ Files: Court Admissible OSINT Without the Cost
New Tool Allows You To Pull Logs from Malicious Telegram Bots
Tool for Exploring Strava Routes on a Map
O’Reilly API Restricts Access, Removing OSINT Source for License Plate Lookups, Here’s An Alternative
TeslaMap: Exposes Recent Location of Tesla Vehicles Around the World
New Affordable Social Media Monitoring Service, Supports LinkedIn and X, With Plans to Add Facebook and Instagram Soon
YouTube Video Finder Tool
Novel Source of OSINF, Video Game Logs, Replay Files
Denmark Joins Group of EU Countries Closing Public Access to Beneficial Ownership Information, Huge Blow to OSINT
New Alternative to Seeker (Honeypot Creation Tool), With Additional Camera Access Feature
Dark Watch, Empowers Counter Human Trafficking Investigators with Real-Time Intelligence, IMB Mapping, and Hospitality Industry Partnerships
Changes Coming in the US Intelligence Community for OSINT
Previous Edition/New Special Edition:
In this special edition of the OSINT Insider, we dived deep into the connections and activities involving North Korean sympathizers, specifically those tied to KFA (Korean Friendship Association). Read more here.
OSINT News/New Tools:
In the last edition, we introduced this new section; now each newsletter comes with a digest of relevant news, tools, etc, for OSINT practitioners, increasing the overall value of the newsletter for readers.
📌 Changes Coming in the US Intelligence Community for OSINT
The US Intelligence community is moving full steam ahead on its initiatives in the world of OSINT, with new OSINT reforms included in the House Permanent Select Committee on Intelligence's fiscal 2026 intelligence authorization act. Some of the notable changes include setting new restrictions around how intelligence components can shift funding away from OSINT activities, standardizing OSINT tradecraft across the IC, and ensuring the accuracy of data. All important efforts to make OSINT a more mature field.

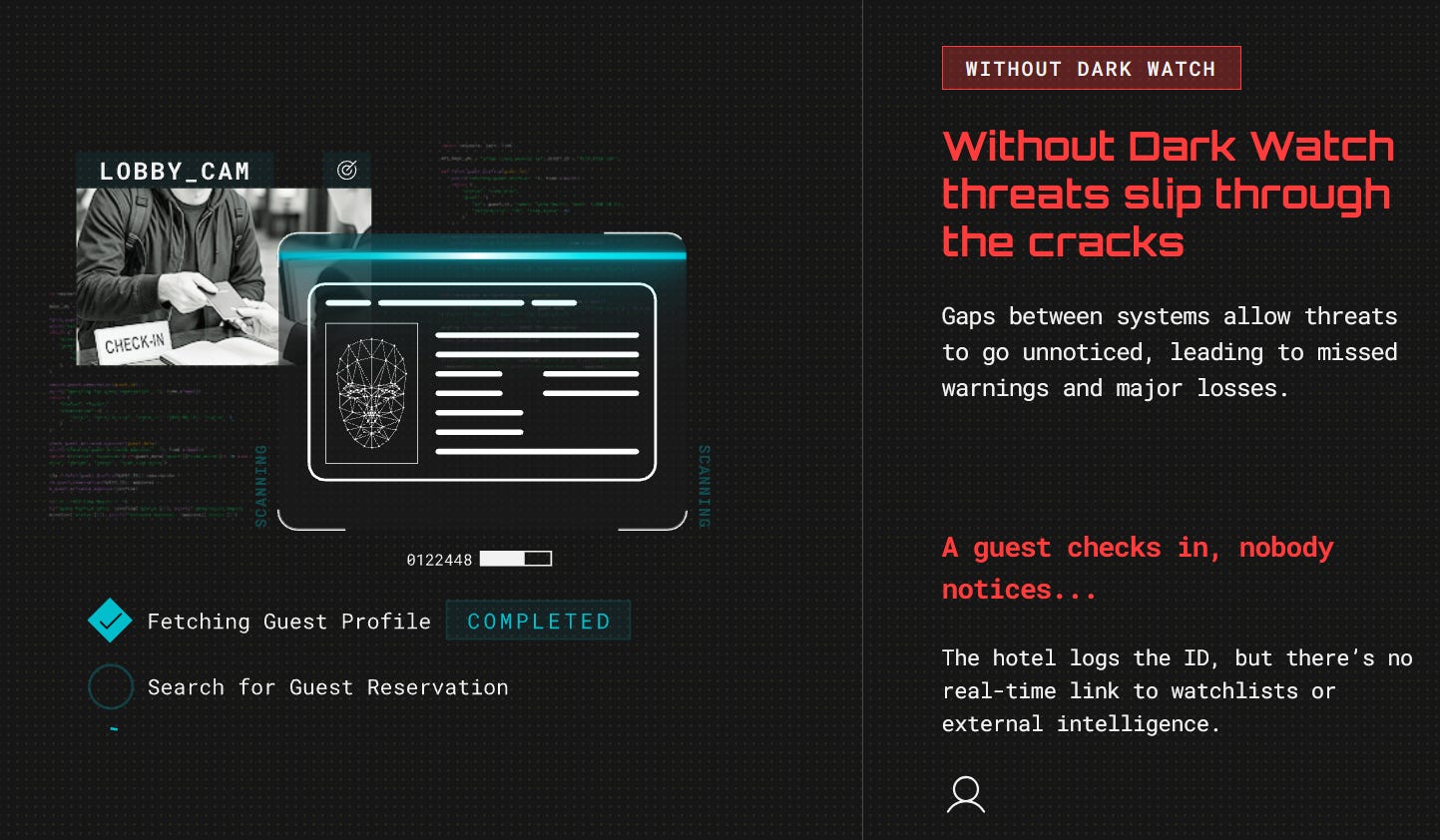
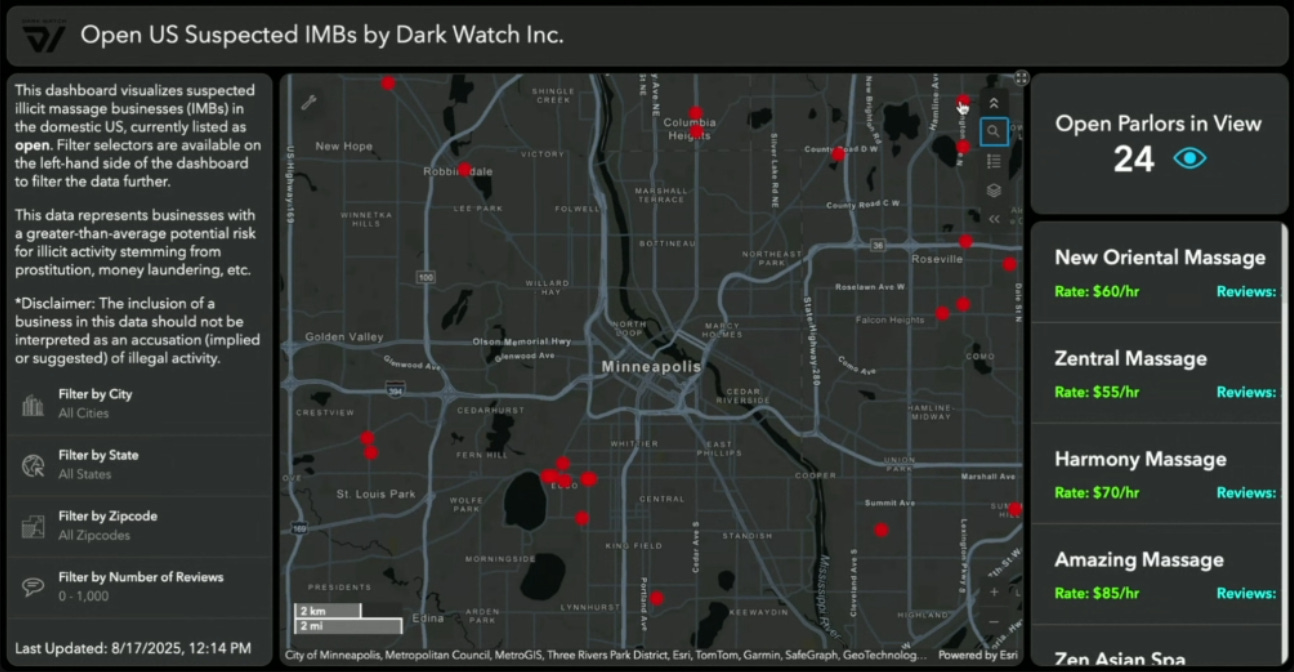
📌 Dark Watch, Empowers Counter Human Trafficking Investigators with Real-Time Intelligence, IMB Mapping, and Hospitality Industry Partnerships
We recently came across a new company called DarkWatch and reached out to learn more about their capabilities. We were amazed at the tech they are building to aid counter-human trafficking efforts.
The two most impressive products we reviewed during our call were the illicit massage parlor maps and the product they provide to the hospitality industry.
Dark Watch provides a product to the hospitality industry that allows them to screen new guests against watchlists and external intelligence. This system not only allows hotels to avoid bad guests that could cause losses, but it can also help investigators track human traffickers around the country. This type of partnership is a game-changer, and the more their network of hospitality customers grows, the harder it is for human traffickers to get away with their atrocities.
The second product we reviewed that Dark Watch offers is a system that finds and maps suspected illicit massage businesses around the country. They scrape data from hundreds of sources, including review sites frequented by Johns. This is a great resource for law enforcement looking to target sex trafficking happening in their cities, as IMBs remain one of, if not the most common, ways people are sex trafficked in the United States.
While many organizations are going after human trafficking, far too many focus on flashy numbers and arrests/stings that have little effect on the overall problem of human trafficking and sex trafficking. This is because when one IMB closes, another opens, when one pimp is arrested, another takes their place, when one sick pedophile is caught, another is born, when one cartel is toppled, another rises, etc. These solutions are the complete opposite of what we have seen from this space; they aren’t trying to play the cat-and-mouse game themselves, they are building tools to make the cats (law enforcement officers, state counter human trafficking task forces, hospitality businesses, etc) much, much more effective at stopping human trafficking.
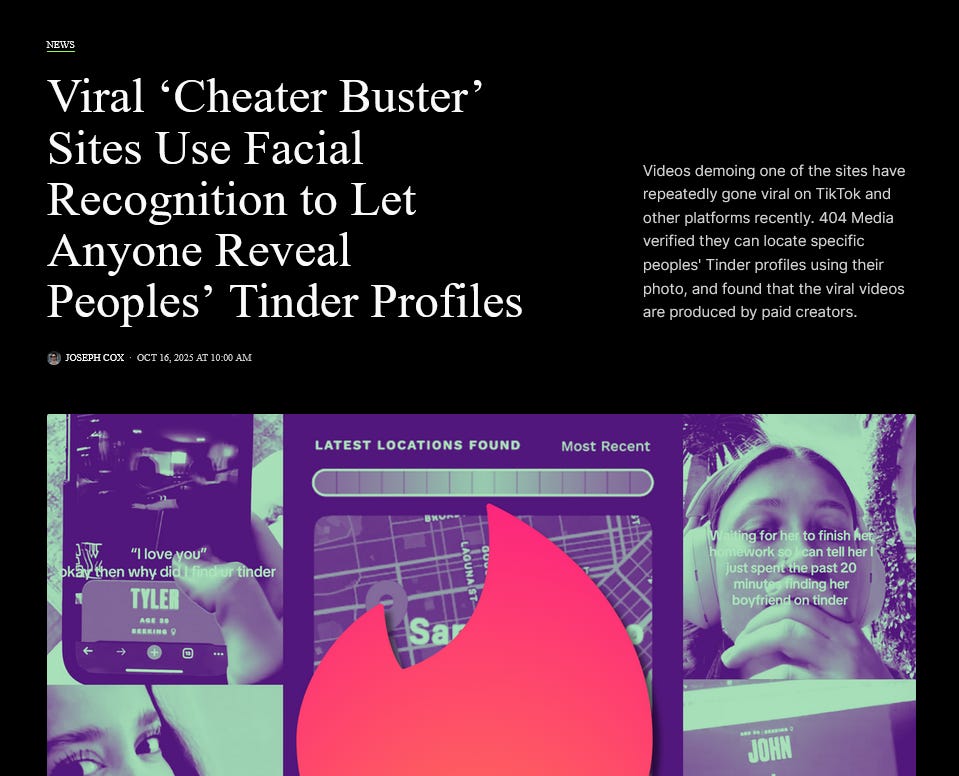
📌 New Dating App Lookup Tool, Powerful Resource for Private Investigators, Could Aid in Pedophile Sting Operations, Infidelity Investigations
404media recently did a deep dive into two tools that allow you to find someone’s dating app profiles by both facial recognition and plain old name lookup. They did their own testing of the apps and proved they work. While 404media isn’t a fan of these apps, for the obvious privacy implications, we think these resources could be invaluable for private investigators working on infidelity cases. It could also be helpful for investigating child predators, allowing them to locate the profiles of known predators (such as by using the sex offenders registry) and attempt sting operations.
As of right now, only CheaterBuster has been tested and proven to work. However, there are many copycat sites, including ones going by CheatEye, that may also be effective in the event that CheaterBuster is no longer available.
https://www.cheaterbuster.com/
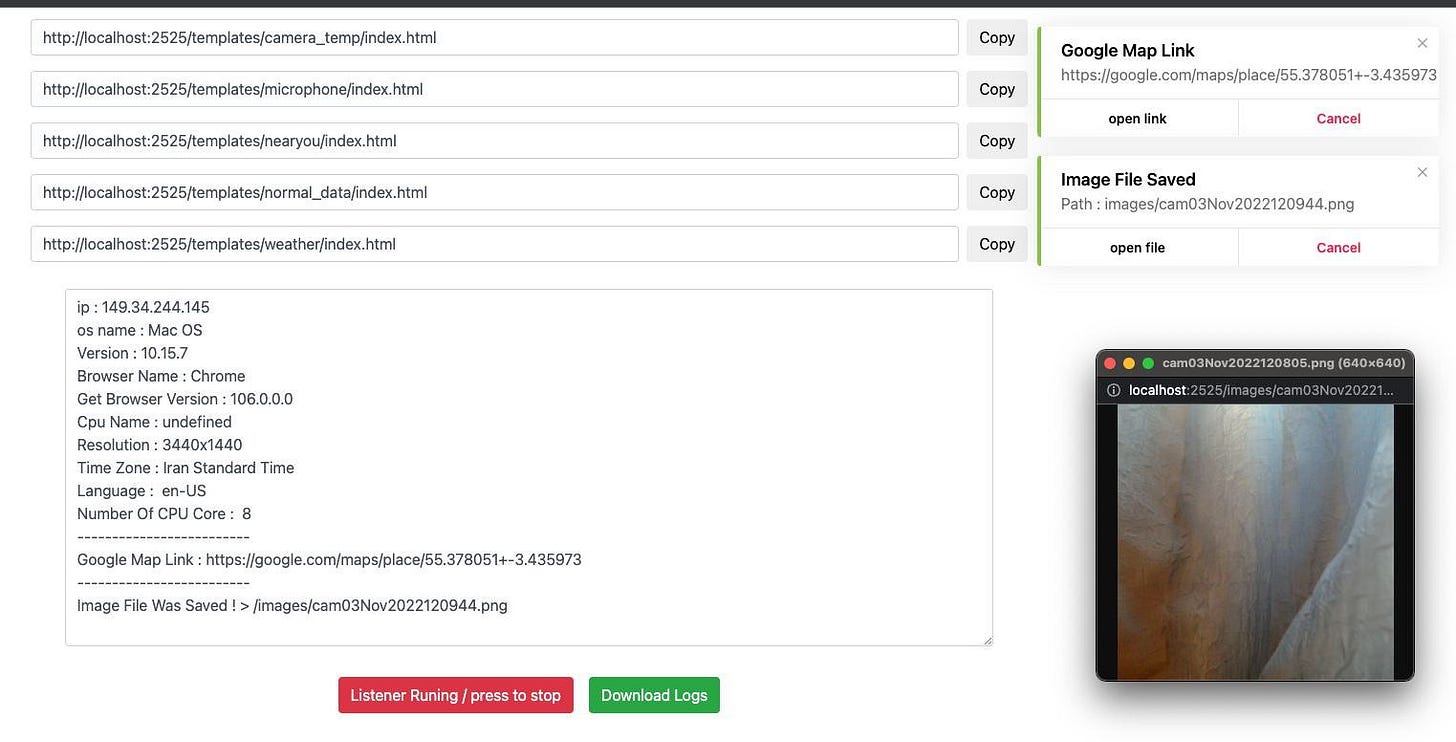
📌 New Alternative to Seeker (Honeypot Creation Tool), With Additional Camera Access Feature
We previously wrote a guide on creating powerful honeypots using an open source tool called Seeker:
This new resource has the same GPS geolocation functionality and built-in social engineering templates, but with additional intelligence collection features, including camera access attempts that, if successful, give the operator audio and video access to the subject for as long as they have the page open.
https://github.com/ultrasecurity/Storm-Breaker/tree/main
📌 New Tool Allows You To Pull Logs from Malicious Telegram Bots
A useful tool that allows you to take Telegram bot API keys from malware uploaded to sites like Any.run, and automate the process of retrieving data that is actively being sent to those Telegram bots. Very helpful for researchers monitoring malicious infrastructure, such as that tied to infostealer malware.
Demo video below:
https://github.com/0x6rss/matkap
📌 Denmark Joins Group of EU Countries Closing Public Access to Beneficial Ownership Information, Huge Blow to OSINT
The Court of Justice of the European Union (CJEU) ruled in 2022 that certain provisions of the EU’s Anti-Money Laundering Directive, which required public access to beneficial ownership information, were annulled. This decision has led to varied access to beneficial ownership information across EU member states, including Germany, Ireland, the Netherlands, and now Denmark.
As of September 1, 2025, Denmark has implemented new rules that restrict public access to beneficial ownership information in the Central Business Register (CVR). This change follows a ruling by the EU Court of Justice, which determined that unrestricted access to such data infringes on privacy rights.
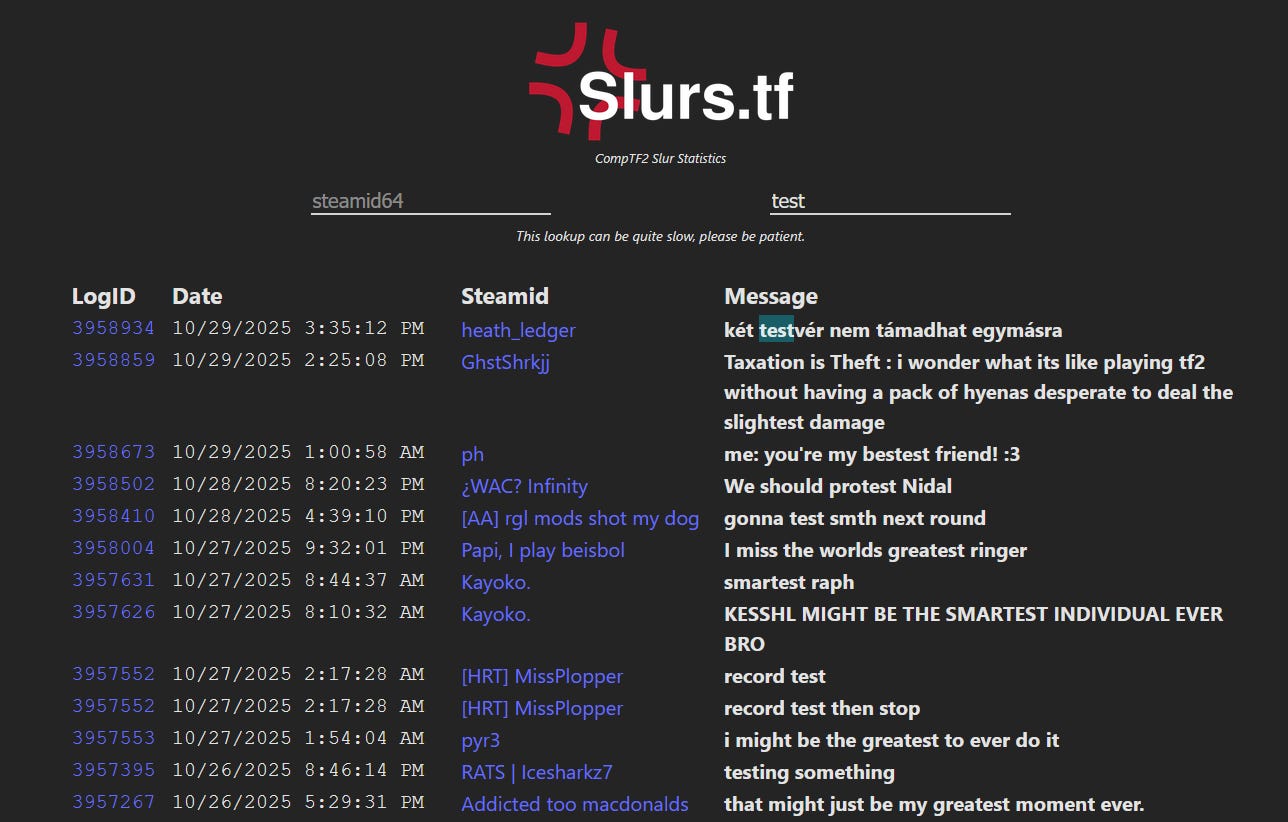
📌 Novel Source of OSINF, Video Game Logs, Replay Files
We recently came across a tool called slurs.tf that compiles logs from Team Fortress 2 gameplay and makes the chat logs of those games searchable via keyword or playername/steamID. This could be an invaluable resource, and Team Fortress 2 isn’t the only game where you can download such log files, also called replay files. This data could be operationalized for other games, too, and the files could be pulled from various locations, including speedrunning and community-run leaderboard websites (which often require you to provide replay files for new records).
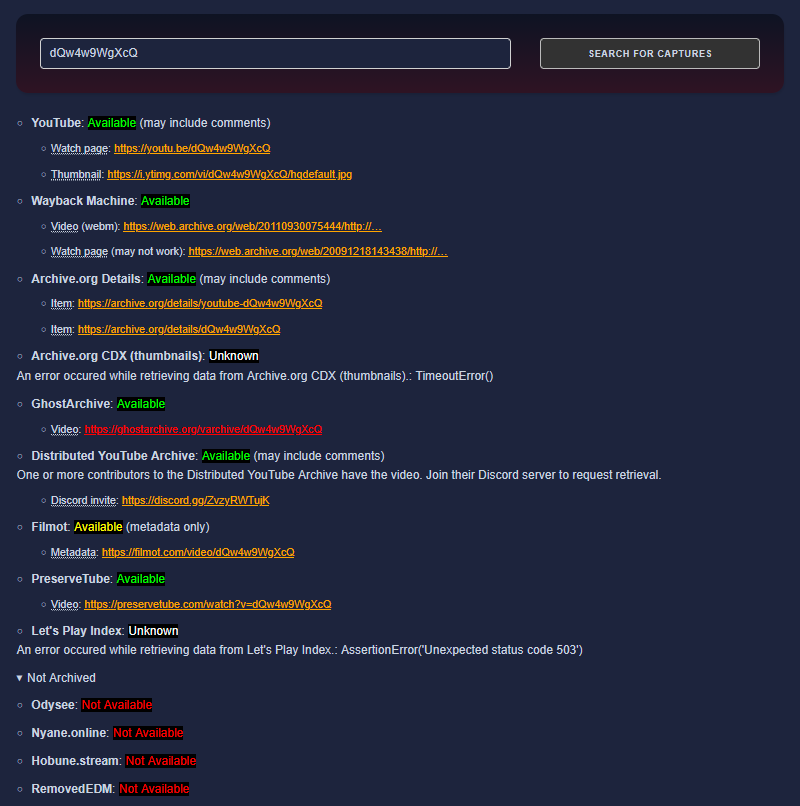
📌 YouTube Video Finder Tool
An open source tool for finding archives of YouTube videos. Must have a link to the original video itself (even if the video is deleted or otherwise no longer available at the link). It can find copies of the video itself and archived metadata such as the title, description, thumbnail, and so on. The tool currently supports the following sources:
YouTube
Wayback Machine
Archive.org Details
Archive.org CDX (thumbnails)
GhostArchive
Distributed YouTube Archive
Hobune.stream
Filmot
RemovedEDM
Odysee
PreserveTube
Nyane.online
Let’s Play Index
https://findyoutubevideo.thetechrobo.ca/
📌 Doogle.gg - A Ridiculously Powerful OSINT Tool for Discord, Could Be Used to Solve Cold Cases
A new Discord tool has emerged that utilizes the data collected by a Discord bot. Not just any Discord bot, but one of the largest bots used for verifying your Discord account when joining new servers, Double Counter. The bot works by requiring you to link your Discord account to their website and collecting basic information like your IP address. This is then used to detect accounts in their database that share the same IP address and prevent those accounts from joining Discord servers across multiple accounts. This was originally used to prevent ban evasion by effectively blocking alt accounts. But now you can query their entire Database by Discord username on Doogle.gg, allowing you to identify other Discord accounts that may belong to someone. This tool could be invaluable for finding new leads on long-dead cases of pedophilia and other crimes that happened via Discord. If you had a case where a Discord account was your only lead, this tool may help you find accounts linked to it, potentially opening up cold cases!
NoTextToSpeech, a popular Discord-centric YouTuber, produced a great video on this topic and the privacy implications of this new tool (including how you can opt out):
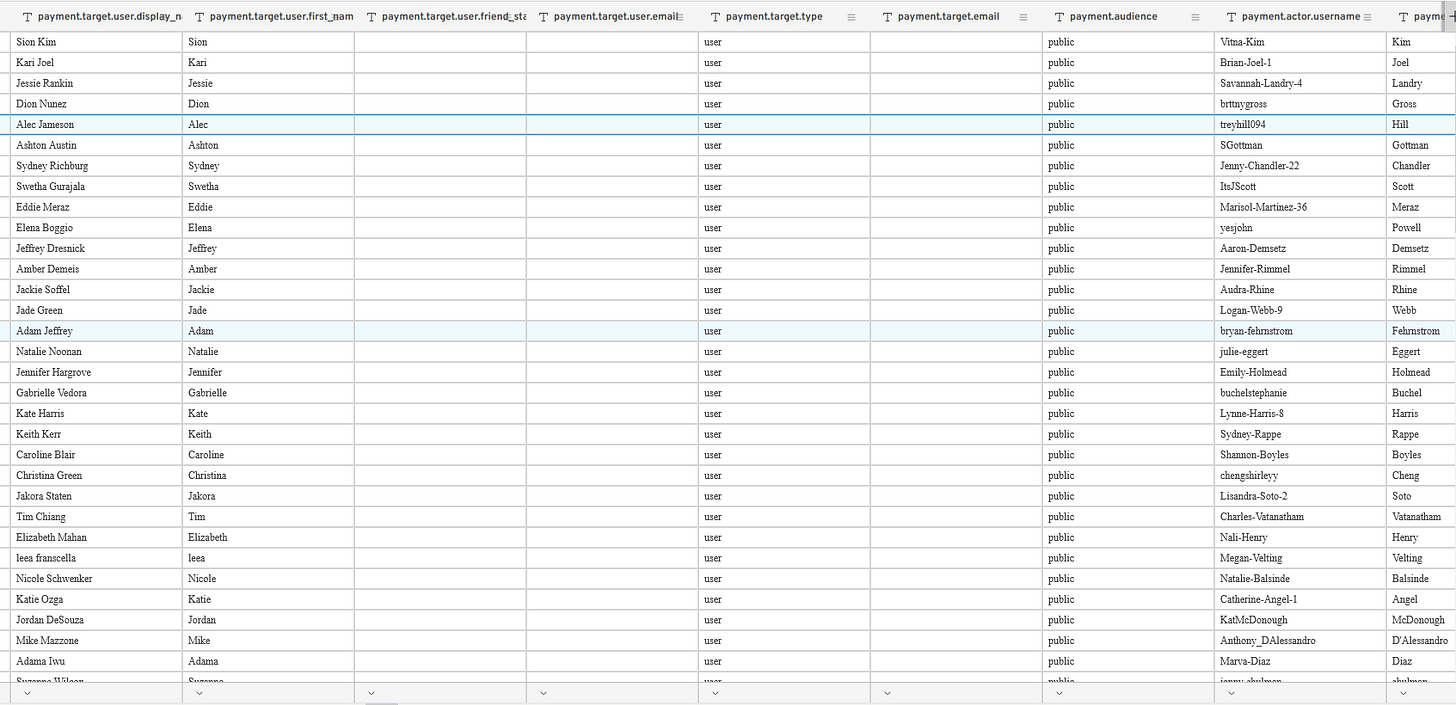
📌 Massive Venmo Transaction Scrape, Downloadable and Searchable Database
Transactions scraped from the Venmo public API.
The data was collected during the following date ranges:
July 2018 - September 2018
October 2018
Jan 2019 - Feb 2019
While there is no data for the amount transferred, it does include the following fields:
date_updated
app.description (Venmo for iPhone, Venmo for Android, etc)
comments.count
payment.id
payment.target.user.username
payment.target.user.last_name
payment.target.user.is_group
payment.target.user.is_active
payment.target.user.profile_picture_url
payment.target.user.is_blocked
payment.target.user.id
payment.target.user.display_name
payment.target.user.first_name
payment.target.type
payment.audience
payment.actor.username
payment.actor.last_name
payment.actor.is_group
payment.actor.is_active
payment.actor.profile_picture_url
payment.actor.is_blocked
payment.actor.id
payment.actor.about
payment.actor.display_name
payment.actor.first_name
payment.note
payment.action
payment.date_created
audience
likes.count
and more!
You can use their Gigasheet to search the date here: https://app.gigasheet.com/spreadsheet/Venmo-Transactions-by-Dan-Salmon-github-com-sa7mon-venmo-data/56db56e2_acb7_4cc9_9d7a_ae308f5a2a06?public=true
Or download the data sets directly:
Torrent: https://github.com/sa7mon/venmo-data/raw/master/venmo.tar.xz.torrent
HTTPS: https://drive.google.com/drive/folders/1m59TMADiwk3gArT-teUUOBlSKokq51ZL
https://github.com/sa7mon/venmo-data
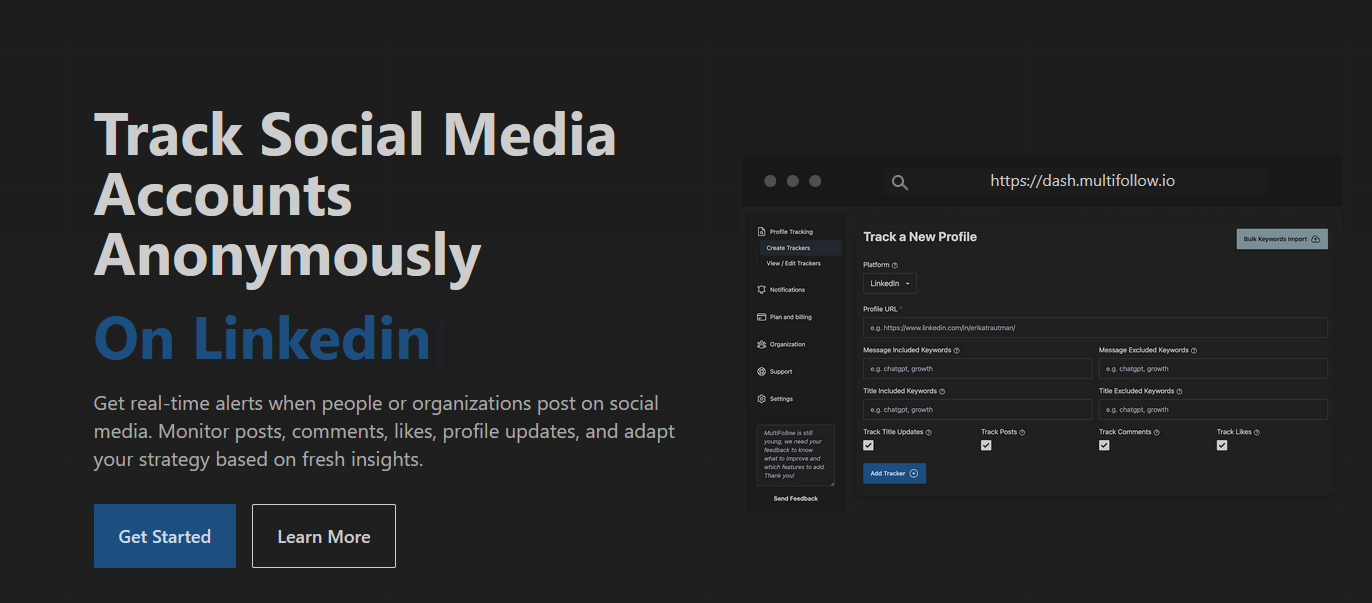
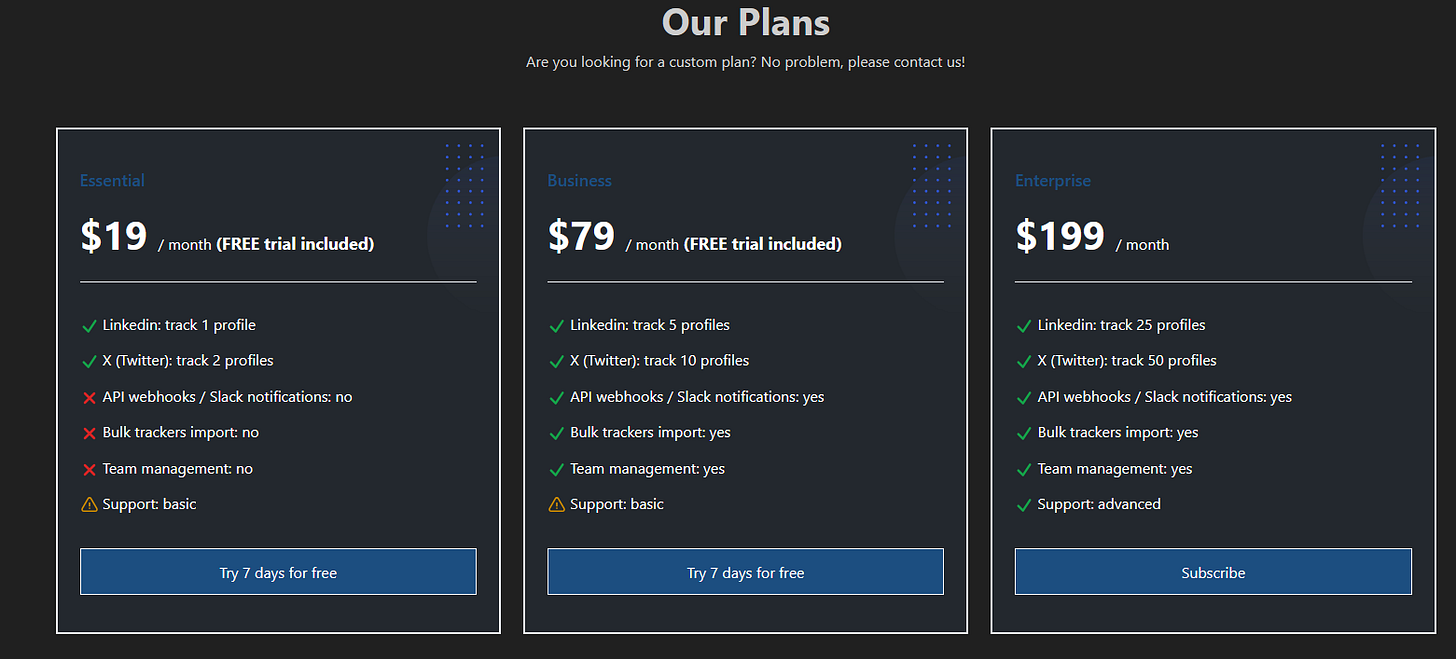
📌 New Affordable Social Media Monitoring Service, Supports LinkedIn and X, With Plans to Add Facebook and Instagram Soon
We came across this tool being shared on prominent OSINT subreddits recently, and were surprised by how affordable the service is in comparison to major social listening platforms that can cost 10’s of thousands a year.
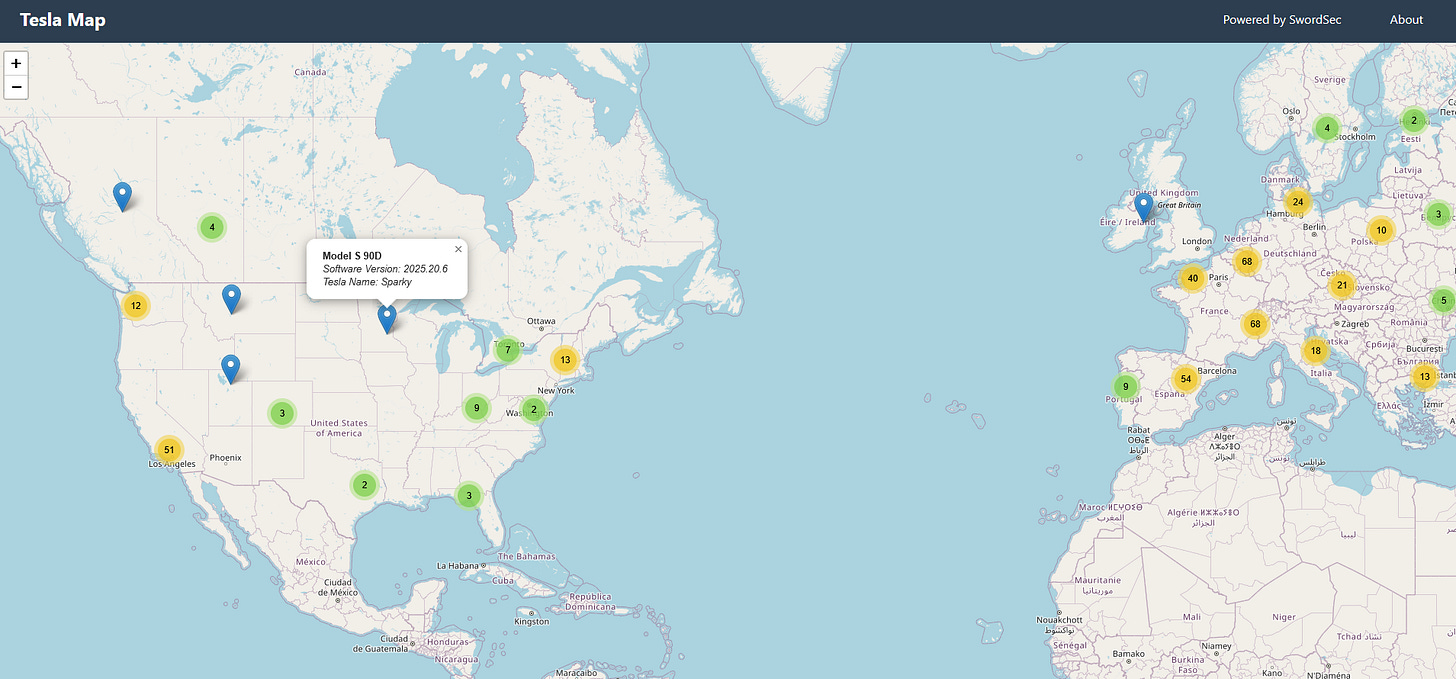
📌 TeslaMap: Exposes Recent Location of Tesla Vehicles Around the World
This map shows the recent location of Tesla cars exposed by the faulty deployment of the TeslaMate software.
📌 O'Reilly API Restricts Access, Removing OSINT Source for License Plate Lookups, Here’s An Alternative
O’Reilly had an API that OSINTers discovered anyone could query for free with a license plate number and receive helpful information about the vehicle, including potentially the VIN and recent service visits. The cheapest legal alternative with similar data we could find was https://licenselookup.org/, which allows you to go from the license plate to the VIN number for just a few cents per query. This data is important because, for OSINTers, in many cases, you do not start with the VIN or even a full license plate number, so having a reliable, cheap way to get that information starting with a long list of potential license plate numbers, is quite helpful.
We recently used this data, paired with VIN lookup sites that can pull information like model number, manufacturer, year, etc, to help narrow down the correct license plate number for a victim of a hit and run incident, something we couldn’t do if we had to pay several dollars to a site like CarFax for each license plate number we wanted to check from the list.
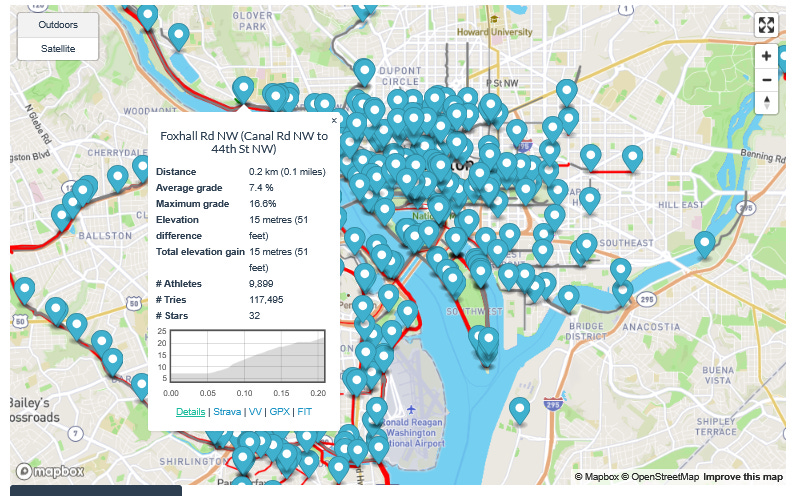
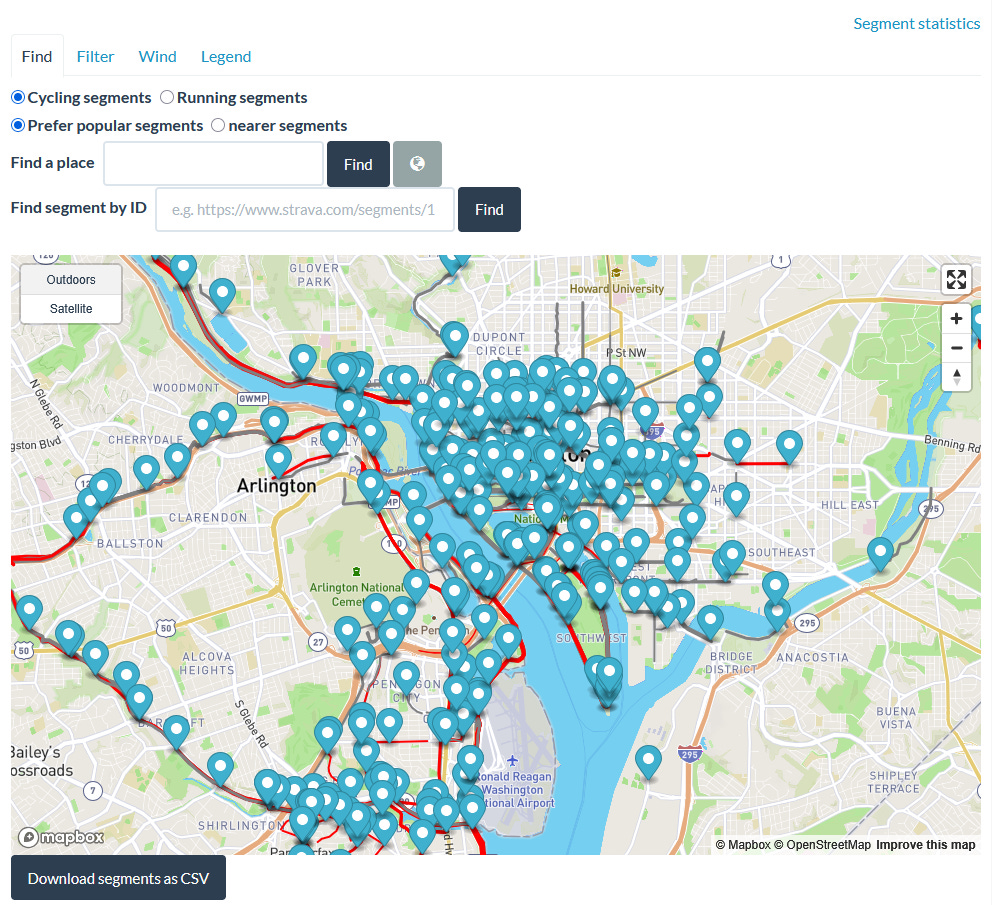
📌 Tool for Exploring Strava Routes on a Map
A new tool for finding Strava running/bicycling routes; it displays routes on a map so you can browse various routes from a particular area of interest. When you’ve identified a route, you can easily view more information about it and go straight to the author’s Strava profile to learn more about them:
https://www.doogal.co.uk/SegmentExplorer
Advertisement/Promotion
infostealers.info
🔗 URL: https://infostealers.info/invite/712CAE1F
🛡️ Defanged: [https://infostealers[.]info/invite/712CAE1F]
Summary: Infostealer data is the new breach data, with billions of records publicly accessible online; it’s nonsensical not to make use of this powerful new OSINT data source.
And unlike breach data, which only reveals a single record from a single company, infostealer data is a subject’s entire digital footprint. Every website they saved a password to, the URL of every website that stored a cookie on their device (yes, even those ones), the names of their files and folders, their saved payment methods, and autofill data, it’s a treasure trove for digital investigators.
When you get a hit, the case is over; you have everything you need. Use it to identify users of CSAM distribution websites or cybercrime forums, use it to make an incredible leads list of your competitor’s product, make it your skiptracing or phone append super power, the potential is truly unlimited with this new datasource. Sign up for infostealers.info today and get 3 free demo searches!Data Available:
Saved passwords and logins from the browsers of over 50 million devices around the world (also contains the URL the password was saved to, providing a powerful digital footprint), over 20 billion records in total
Autofill data (Can include information like full name, billing addresses, shipping addresses, contact information, or anything else someone might save to their browser)
Search By:
Phone Number
Email Address
Username
Domain
Password
Any Keyword - Name, Address, etc (Mostly restricted to autofill data searches)
COMP ID (Gets all of the data from a specific device)
NEW - Crypto Currency Address (Only available in the full platform @ info.fwintel.com) - Only Solana and ERC20 addresses are supported currently.
Cost: $1 per credit
Non-pro accounts will have a censored password field everywhere to prevent misuse of data; the URL field remains uncensored everywhere, and the login field is only very partially censored in domain search results to prevent misuse.
$200 per year for Pro access (requires KYC) to get all results, including the censored results.
Other Important Details:
The full password and autofill field values are censored for users who have not successfully undergone KYC. Only the URL and Login field are visible for non-KYCed users in order to prevent misuse of the data.
Additionally, no cookie data is provided in this platform whatsoever. We specifically do this to prevent account hijacking, the most dangerous potential use of infostealer data.
It’s recommended to use infostealer data as a starting point and then perform parallel reconstruction efforts, as this data may not be admissible in court under the fruit of the poison tree doctrine.
The full platform provides additional data from infostealer logs in search results, such as stored cookies (acts as a pseudo browsing history), autofill data (can include addresses), saved payment methods (credit cards), and system information (file tree). You can also export the raw contents of the logs, which contains information vital for incident response (exact time of infection, device hostname, IP address, directory of infection, etc), and even more data like actual browsing history, desktop screenshots, installed programs, cryptowallet information, and more. And you can search using more advanced search features, including keyword searches (with boolean and wildcard support), searches against URLs, credit card numbers, file/folder name search, and more! Learn more about the full platform here, and reach out for a trial: https://www.farnsworthintelligence.com/infostealer-data
Sign up to get 3 free demo search credits to test out the product!
Law enforcement working in ICAC units can reach out for free access at: lea@farnsworthintelligence.com
📌 WACZ Files: Court Admissible OSINT Without the Cost
While we’ve covered this before, this is a reminder that WACZ files allow for extremely high-fidelity court-admissible archives of websites, including those of dynamic sites like Facebook. If you use WebRecorder’s Chrome extension, you can also bypass typical anti-bot measures that would break the archive if it were collected from a service like WayBackMachine. We highly recommend the WebRecorder software for making high-quality admissible archives of websites. It’s free, it’s widely supported, and it’s standardized. There’s also a plethora of tools for working with WACZ files because of its wide industry adoption. Perfect for folks who need court-admissible archives, but cannot justify or afford to pay for services from companies like ForensicOSINT, Hunchly, etc.
If you are worried this might not be court-admissible, we’d recommend reviewing the standard specifications of the WACZ file format, which includes the common features advertised by the aforementioned paid tools, such as file hashing, timestamps, etc, as well as additional features that allow it to self-error correct and detect issues within the archive: https://specs.webrecorder.net/wacz/1.1.1/
The open-source nature of the WACZ file format and tooling also helps make it more defensible, as industry experts are able to verify the efficacy of the file format and technology in use by reviewing the code and specifications. Whereas with private tooling, a defense could argue that there is no way to verify that the tooling correctly archived the files or that something couldn’t have been included in the code that modified the files. Its open-source and transparent nature adds defensibility to the file format.
With WACZ files, you can even host file fidelity archives of pages for your clients, allowing them to view them as if they were still live (helpful for deleted accounts, impressive in a courtroom): https://webrecorder.net/replaywebpage/ (Also can be done using Perma.cc)
The WACZ file format and associated tools aren’t just good; they’re the industry standard, utilized by Archive.org and Perma.cc’s platform. Perma.cc is a platform that was developed by the Harvard Innovation Lab to prevent “link rot” and it uses the WACZ file format to achieve this. Perma.cc is now used across the Ivy League, including by Stanford Law: https://guides.law.stanford.edu/perma
We don’t see anything more defensible and useful than this in the space currently.
If you appreciated how much value we put into this free OSINT digest section, please support us with a paid subscription:
OSINT Internship Opportunities
More than half of all interns at Farnsworth Intelligence have now been able to work on real cases by participating in our Junior Analyst program, accessible to all interns regardless of whether they are helping with the knowledge base project or a part of the content/product development internship program. Here’s what one of them had to say about the experience:
”Amazing! Thank you so much for letting us work on this. I learned so much that I would never be able to on my own, and really enjoyed the process! Honestly, all of this was new for me; I’m really at the beginning of my OSINT journey. My experience with OSINT up until this point has been a lot of reading and some Sofia Santos/Bellingcat challenges, so this put together a lot that I read about and exposed me to new tools and analysis.”
We still have many openings for our Content and Product Development Internship, so if you know anyone in the marketing, communications, copywriting, or adjacent fields, we would encourage you to share this exciting opportunity with them: https://www.farnsworthintelligence.com/opportunities#cntproductdevinternship (Direct Link to Internship Listing)
We also just launched a Junior Developer Internship, perfect for anyone looking to gain real development experience for their resume, so if you know anyone in the software development or computer science fields, we would encourage you to share this exciting opportunity with them: https://www.farnsworthintelligence.com/opportunities#jnrdevinternship (Direct Link to Internship Listing)
Find out about our other internship opportunities here: https://www.farnsworthintelligence.com/opportunities
Today’s Post - Exploring the World of Underground OSINT:
Today’s post will focus on a loosely connected network of OSINT tools that primarily serve or market to the notorious online communities (the com) responsible for crimes such as extortion, cyberstalking, financial theft, account hijacking, digital asset theft, SIM swapping, and crypto draining.
Everything we claim in this edition is alleged; we are not lawyers, this is not legal advice, nor are they absolute claims. These are the conclusions we reached based on our expert understanding of the data ecosystem, but for legal reasons, it’s still alleged, and we can’t be 100% certain we are correct without direct access to the backends and architecture of these tools.
Additionally, unlike other posts, we do not recommend or endorse any of the tools we are about to share. In fact, for legal/operational security reasons, we recommend you do NOT use the tools we are going to share. You might also find that some of the tools we listed are already offline. This is due to the effierial nature of this space.
Some of the capabilities of the tools we are going to talk about today include:
Reduced credit prices and/or free access to resources like IntelX, OSINT Industries, Orbitly, and hundreds of other paid tools (through stolen API keys)
Unauthorized/potentially illegal access to regulated data from tools like TLOxp, Tracers, CarFax, and more
Unethical non-KYCed access to incredibly sensitive data, like session keys derived from infostealers
Want to see the rest of this post? You’ll need to become a paid subscriber first:
Keep reading with a 7-day free trial
Subscribe to The OSINT Insider Newsletter to keep reading this post and get 7 days of free access to the full post archives.