OSINT Insider Issue #5 - Network/Internet Infrastructure Tools, How the OSINT Industry is Shifting, Knowledge Base Milestone, and More!
There are many data sources and tools that can be invaluable when digging into digital infrastructure, but some pose hidden risks such as Chinese surveillance on a tools users and their searches!
There are many data sources and tools that can be invaluable when digging into the infrastructure used by threat actors, but they are not all built the same. Some have unique sources of behavioral data on IPs, some provide data that is more reliable or current than others, and some have hidden issues, like the risk of PRC surveillance by anyone who uses it. This article is here to compare these tools, their data sources/capabilities, and allow you to stay on the cutting edge with your intelligence work.
Previous Issue:
In the previous issue, we dived deep into the negative effects of platforms like Skype disappearing without any archive of their data. Allowing important digital history to be forgotten and leaving some digital crimes potentially unsolvable. We also discussed the problems of collecting data to solve this data rot issue and potential solutions to solve those problems. Read more here.
How the OSINT Industry is Shifting
This month, we also presented at OSINTCon 2025 about the future of the OSINT Industry. Our presentation contains deep insights and information that we have been gathering over the past few months about how the OSINT industry is changing, how AI/ML is being used succesfully, the pitalls of LLMs, the rise of consortiums, the shifting intelligence community landscape in the United States, new laws/regulations affecting OSINT globally, and more. This presentation is part of our ongoing effort to provide deep insights to the OSINT community, beyond surface-level information you tend to find elsewhere, and was crafted with our readers in mind:
Here's a link to the Canva slides used in the presentation as well, so you can click the links to sources/additional information found in the presentation: https://www.canva.com/design/DAGoBI2P1w0/Sijma6dG-3AJpVuPtBHPXA/view?utlId=hbb6590b4ea
Upcoming Special Edition on North Korea
We have been hard at work on additional intelligence efforts related to the North Korean ITW (IT Worker) threat. We have finished writing up our new intelligence into a report and will be publishing that research very soon as a special edition of the OSINT Insider.
Thank You
We just surpassed 2,000 subscribers to the OSINT Insider! Thank you all so much for your support!
We especially want to thank all of you who have contributed financially to OSINT Insider; without your support, we simply could not justify spending so much time researching and writing this content for you. Your work also supports the development of the knowledge base, from the infrastructure, to the AI compute needed for the tech we are building to solve OSINT pain points, to administrative costs, to eventually affording staff to maintain the knowledge base itself.
If you appreciate what we do and want to support continued efforts, we invite you to become a paid subscriber.
OSINT Insider Knowledge Base Reaches Milestone
The knowledge base is a key project that paid subscribers are supporting the development of, it contains 1600 reviewed tools and resources, and nearly 2000 tools/resources in total. Our priority in the first phase of this project has been to provide detailed information about every entry in the knowledge base, and thanks to the awe-inspiring work of our 2025 internship cohort, we have already surpassed 10% data enrichment of this massive database. 10’s if not hundreds of thousands of words regarding details like data sources, country of origin, search capabilities, and more were researched and written by these dedicated individuals so far.
Additionally, we introduced a well-deserved junior analyst program to offer these dedicated interns additional opportunities and experience with real case work. We will also soon be scheduling networking events for our interns, where they will be able to speak with professionals within the world of OSINT and learn about different career paths that utilize this discipline. Want to talk with these bright minds from universities like John Hopkins, Penn Sate, University of York, and others about what you do? Then reach out to us!
We still have many openings for our Content and Product Development Internship, so if you know anyone in the marketing, communications, copywriting, or adjacent fields, I would encourage you to share this exciting opportunity with them: https://www.farnsworthintelligence.com/opportunities#cntproductdevinternship (Direct Link to Internship Listing)
We also just launched a Junior Developer Internship, perfect for anyone looking to gain real development experience for their resume, so if you know anyone in the software development or computer science fields, I would encourage you to share this exciting opportunity with them: https://www.farnsworthintelligence.com/opportunities#jnrdevinternship (Direct Link to Internship Listing)
Find out about our other internship opportunities here: https://www.farnsworthintelligence.com/opportunities
Today’s Post, Important Note
Without further ado, today’s post. As a sneak peek at what we are building with this knowledge base, I decided to write MUCH longer descriptions that reflect the depth of information on these tools in our knowledge base. These very long and detailed descriptions are available for the first 10-20 tools, but since we know many of you come here to find new and unique tools/resources, we also included the full list of our collection for this category for paid subscribers. Which includes 40+ tools from unique sources of IP information using PCAP files to super-fast directory busting tools that beat dirbuster in a race any day.
IP Investigation Toolbox
🔗 URL: https://cipher387.github.io/domain_investigation_toolbox/ip.html
🛡️ Defanged: [https://cipher387[.]github[.]io/domain_investigation_toolbox/ip[.]html]
Summary: Simplistic tool for gathering information about IP addresses through 15 linked OSINT tools (e.g., Shodan, Censys).
Cost: Free
Data Available: This tool links to results from:
Censys.io
Shodan.io
Bgp.he.net
Bgp.tools (Prefix)
Spyse.com
Myip.ws
Threatcrowd.org
Ipv4info.com
Grayhatwarfare (Files)
Maltiverse (malware reports)
ThreatMiner
Natlas.io
Check-host.net
iplocation.net
ip2location.com
Search By:
IP Address only (IPv4 and IPv6)
Other Important Details:
The tool does not display the results itself, but provides buttons to go directly to the results page of each listed tool for the provided IP address.
This page/tool was last updated two years ago, however, most of the 15 tools linked on the page still work/are online.
Cyberbro
🔗 URL: https://github.com/stanfrbd/cyberbro
🛡️ Defanged: [https://github[.]com/stanfrbd/cyberbro]
Summary:
A FOSS self-hosted platform for cyber threat intelligence research on indicators of compromise (IP address, file hash, etc). Supports a wide variety of unique and powerful features, including support for Chrome Extension ID lookups, a vast selection of data sources, multiple graphical view options, EDR and CTI platform integrations, automated comprehensive reports, caching, proxying, multi-threading, and more!
Cost: Free, some data sources require an API key to integrate them into this tool and require you to pay for said API key/access.
Data Available:
Pools results from these sources into one interface:
AbuseIPDB
Abusix
Alienvault
Github
Google
Google common DNS records
Hudson Rock
IPquery
MISP (demo from @CIRCL - TLP:CLEAR)
Phishtank
Reverse DNS
RDAP (ex Whois)
Shodan
Spur.us
ThreatFox
URLscan
VirusTotal
Search By:
IP Address
Domain Name
File Hash
Chrome Extension ID
Or bulk upload IoCs/selectors (plain text, separated, HTML, JSON, CSV, log data, garbage data, fanged data [.] [dot] hxxp, etc.)
Other Important Details:
Self-Hosted: The software can be tested via the free demo page and self-hosted locally on your machine.
Easy Input: Paste raw logs or IoCs—automatic parsing and extraction.
Multi-Service Checks: Reputation lookup for IPs, hashes, domains, URLs, and Chrome extension IDs across many threat intel services.
Comprehensive Reports: Advanced search, filtering, and export to CSV/Excel.
Fast Processing: Multithreaded for speed.
Automated Pivoting: Discover related domains, URLs, and IPs via reverse DNS and RDAP.
Accurate Domain & Abuse Info: ICANN RDAP and abuse contact lookups.
Integrations: Microsoft Defender for Endpoint, CrowdStrike, OpenCTI, Grep.App, Hudson Rock, and more.
Proxy & Storage: Proxy support and results are stored in SQLite.
History & Graphs: Analysis history and experimental graph view.
Cache: Caching for faster repeat lookups (enabled at multi-engines level, not each engine).
The lead developers/contributors are actively maintaining and improving this project as of this article’s writing.
Advertisement/Promotion
infostealers.info
🔗 URL: https://infostealers.info/invite/712CAE1F
🛡️ Defanged: [https://infostealers[.]info/invite/712CAE1F]
Summary: Infostealer data is the new breach data, with billions of records publicly accessible online; it’s nonsensical not to make use of this powerful new OSINT data source. And unlike breach data, which only reveals a single record from a single company, infostealer data is a subject’s entire digital footprint. Every website they saved a password to, the URL of every website that stored a cookie on their device (yes, even those ones), the names of their files and folders, their saved payment methods, and autofill data, it’s a treasure trove for digital investigators. And when you get a hit, the case is over, you have everything you need. Use it to identify users of CSAM distribution websites or cybercrime forums, use it to find the smoking gun for your high-dollar divorce case, the potential is truly unlimited with this new datasource. Sign up for infostealers.info today and get 3 free demo searches!
Cost: $1 per credit (most searches only cost 1 credit per search)
Data Available:
Saved passwords and logins from the browsers of over 50 million devices around the world (also contains the URL the password was saved too)
Search By:
Phone Number
Email Address
Username
Domain
Password
COMP ID (Gets all of the data from a specific device)
Other Important Details:
The full platform provides additional data from infostealer logs in search results, such as stored cookies (acts as a pseudo browsing history), autofill data (can include addresses), saved payment methods (credit cards), and system information (file tree). You can also export the raw contents of the logs, which can contain even more data like actual browsing history, desktop screenshots, installed programs, cryptowallet information, and more. And you can search using more advanced search features, including keyword searches (with boolean and wildcard support), searches of credit card numbers, file/folder name search, and more! Learn more about the full platform here, and reach out for a trial: https://www.farnsworthintelligence.com/infostealer-data
Prerequisite Knowledge Before Continuing:
There is some basic required knowledge to understand the capabilities of the internet-asset searching tools listed below. Specifically, you need to understand how they collect information about the “technologies” or “services” they catalogue. This information is collected through what is known as a banner.
This is an explanation of a banner and what it contains from Shodan:
FOFA
🔗 URL: https://en.fofa.info/
🛡️ Defanged: [https://en[.]fofa[.]info/]
Summary: Chinese-based CTI cyberspace asset search engine designed for mapping the global internet landscape. It actively detects IoT devices— both hardware and software— utilizing an extensive database of over 350,000 fingerprints. Use with caution and don’t provide any sensitive information, however, as the company is subject to PRC surveillance.
Cost: Freemium
Data Available:
Banner Information
Fingerprint-based Products List (Ex: Kubernetes, Linux, etc)
Open Ports/Services
Search By:
IP Address
Supports batch search up to 100 at a time, and IP ranges via batch search
Domain Name
Supports batch search up to 50 at a time
Icon (Favicon/.ico)
Full-text/keyword search (finds matches in banner information)
Other Important Details:
The parent company of this platform is called “Beijing Huashun Xin'an Technology Co., Ltd.” and its office address is listed as: 11th Floor, Building C, Hehua Mingcheng Building, No. 7 Jianguomen South Street, Dongcheng District, Beijing. By Chinese law, all Chinese companies are subject to surveillance by the Chinese government, and all of their data is accessible to the PRC. Because of these laws, it is ill-advised to use this tool for anything classified or confidential.
The Chinese version of the platform includes a “Data Rewards Program”, which is described as this when translated from Simplified Chinese:
“FOFA invites white hat masters to build a data map and submit the assets not found by FOFA.
Once the submission is automatically redeemed for F-point, any questions can be contacted by Fofabot.”
The parent company of FOFA is a Beijing-based cybersecurity and asset monitoring company. Its’ customer base includes some notable Chinese companies:
Spur
🔗 URL: https://spur.us/context-api/
🛡️ Defanged: [https://spur[.]us/context-api/]
Summary: Identifies anonymization (e.g., VPNs, mobile proxies, residential proxies, etc.) networks tied to IP addresses. We used this tool when investigating some of the North Korean IPs that we gathered for our report on North Korean ITW farms.
Cost: Freemium Model
Data Available:
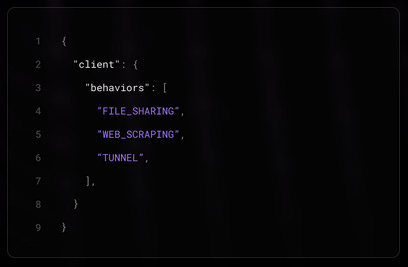
Real-time identification/behavioral information about IP addresses:
VPNs tied to a specific IP
Residential proxies tied to a specific IP
Behaviors tied to a specific IP
Search By:
IP Address (IPv4 or IPv6)
Other Important Details:
You can also purchase raw data feeds that can be used for searches other than search by IP, such as historical records, searching all the IPs available for a single anonymity service on a given day, or all of the infected IPs contributing to a malware proxy service.
Spur collects its data by signing up for VPN/Proxy services and collecting the exit/entry IPs directly from them. Meaning the data is much more reliable and verbose than the labels by IPInfo, for example.
StopForumSpam
🔗 URL: https://www.stopforumspam.com/usage
🛡️ Defanged: [https://www[.]stopforumspam[.]com/usage]
Summary: A free service that records reports of spam on forums, blogs, and wikis and provides the data back to those sites via integrations. Often used to detect potential spammers at the new user registration step or at other events, such as a new post. Effectively serves as a universal blacklist for spammers; used on over 200,000 sites.
Cost: Free
Data Available:
Each report in their database can contain the following information:
Date of Report
IP Address
Email Address
Username
Country
Some records also contain an evidence report, which provides additional details like spam count, explanation of how they were caught/were spamming, last seen date, etc.
Search By:
This tool uses a Google CSE to support full-text/keyword search of all reports on the site, so you can search for anything that could be in the reports (refer to the data available section). Relevant supported selectors include:
IP Address (IPv4 Only)
Email Address
Username
Other Important Details:
Nothing to note.
WebCheck
🔗 URL: https://web-check.xyz/
🛡️ Defanged: [https://web-check[.]xyz/]
Summary: All-in-one website investigation tool designed for comprehensive analysis. Performs over 30 checks, looking at IP information, SSL chain, DNS records, cookies, headers, and more. Web Check is available as a hosted version, and it can be deployed locally via Docker or source code.
Cost: Free
Data Available:
Pulls the following data points based on URL:
IP Info
SSL Chain
DNS Records
Cookies
Crawl Rules
Headers
Quality Metrics
Server Location
Associated Hosts
Redirect Chain
TXT Records
Server Status
Open Ports
Traceroute
Carbon Footprint
Server Info
Whois Lookup
Domain Info
DNS Security Extensions
Site Features
HTTP Strict Transport Security
DNS Server
Tech Stack
Listed Pages
Security.txt
Linked Pages
Social Tags
Email Configuration
Firewall Detection
HTTP Security Features
Archive History
Global Ranking
Block Detection
Malware & Phishing Detection
TLS Cipher Suites
TLS Security Config
TLS Handshake Simulation
Screenshot of Website
Search By:
URL
Other Important Details:
Nothing of note.
Netlas.io
🔗 URL: https://app.netlas.io/host/
🛡️ Defanged: [https://app[.]netlas[.]io/host/]
Summary: Netlas.io is positioned as an internet scanning and search engine platform, providing data on internet-connected assets, including hosts, services, DNS records, WHOIS information, SSL certificates, etc. It caters to cybersecurity professionals, OSINT investigators, and threat intelligence analysts, offering tools for discovery, reconnaissance, vulnerability assessment, and attack surface mapping.
Cost: Freemium Model
Data Available:
WhoIS information
SSL certificates
DNS records
Banner responses/services
Search By:
Supports advanced boolean searches using the following fields/options:
Note: Many of these fields are only available with a paid subscription to the website.
Addressing:
domain
host
host_type
IP
path
port
prot4
prot7
protocol
referer
target
uri
Information:
certificate
cve
geo
isp
jarm
tag
whois
Protocols:
amqp
dns
elasticsearch
ftp
http
imapmemcached
modbus
mongodb
mqtt
mssql
mysql
netbios
ntp
oracle
pop3
postgres
raw_tcp
rdp
redis
s7
smb
smtp
snmp
socks
ssh
t3
telnet
vnc
Service fields (from Netlas themselves):
@timestamp
last_updated
scan_date
Other Important Details:
Includes multiple paid and free datasets in their DataStore, including:
Free - Top 1,000 most common subdomains: A dictionary containing the top thousand of the most commonly used subdomain names sorted by frequency of use.
Netlas does not disclose how often they perform scans, using a vague “scans the internet from time to time” explanation. This makes it unclear how it compares to a service like Shodan, which advertises weekly internet-wide scans.
The number of searches and the number of results are limited for free users.
Includes a graphical search/discovery feature:
Shodan
🔗 URL: https://www.shodan.io/
🛡️ Defanged: [https://www[.]shodan[.]io/]
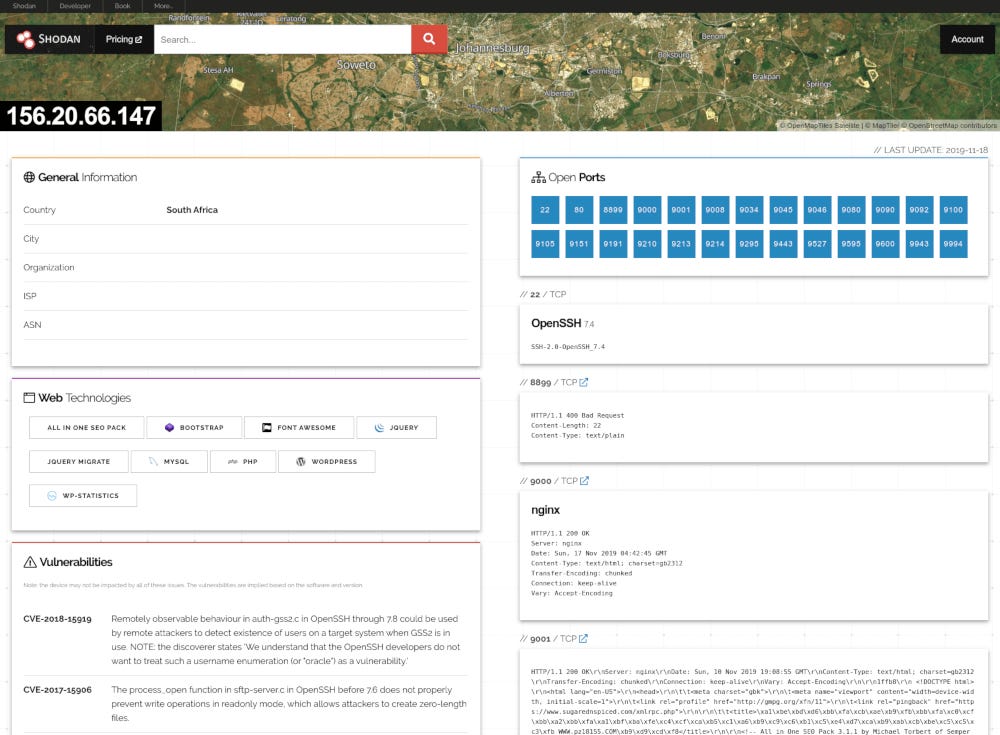
Summary: A Specialized search engine for internet-connected devices. Also known as the search engine for the Internet of Things (IoT), it operates by scanning the internet, collecting service banners from open ports, and making this data searchable. It was the first search engine of its kind at launch.
Cost: Freemium model
Data Available:
Technologies identified (e.x. OpenSSH, nginx, etc)
Provides full data property of banner text response that was used to identify the technology on a specific port (e.x. “SSH-2.0-OpenSSH_7.4” response on port 22 to identify OpenSSH)
Open Ports
Vulnerabilities Identified
Includes the CVE
Search By:
IP Address
Domain Name
Keywords in Data Field, Most Commonly Used to Search By Technology/Service (e.x. openSSH, nginx, etc)
Keywords in All Other Fields in Banner Response (using filters)
Other Important Details:
Shodan claims to crawl the entire internet every week.
As part of their enterprise offerings, Shodan sells a bulk DataFeed where organizations can download all of the data that Shodan collects to build their own database of Internet-connected devices. However, it is likely (but we have not confirmed this) they would have terms to restrict this to internal use only to prevent you from creating a competing platform with their data.
Their enterprise offerings also include on-demand scanning, allowing you to use their infrastructure for your needs.
Shodan was the first internet-wide search engine of it’s kind at launch and is the most popular/well-known amongst its peers.
Making searches using filters (which includes any searches that search properties other than the data property from the banner response) is limited to paid users.
The number of results and number of searches are limited for free users.
GreyNoise Visualizer
🔗 URL: https://viz.greynoise.io/
🛡️ Defanged: [https://viz[.]greynoise[.]io/]
Summary: Threat intelligence platform that utilizes internet-wide scanning and analyzes exploitation traffic. Differentiates between “noise” (e.g., scans from search engines, legitimate security companies, etc.) and potentially malicious scanning or targeted attack traffic. It offers fully customizable filters and visualizations. It can help analysts gain context on observed IP addresses.
Cost: Freemium
Data Available:
Note: All of the data they have is also historical in nature, you can view when events/records were logged and view a timeline of activity for a specific IP address. You can view up to the last 90 days of it for free as well.
rDNS
rDNS is short for reverse DNS, it refers to DNS records tied to the IP address. This can be used to identify domains or subdomains pointing to the IP address.
Actor
This field is a label provided by Greynoise that correlates to the threat group/actor tied to an IP address. It can be very useful information for threat intelligence research.
Observed Activity
This is data that is logged by Greynoise or other sources that provides context into the activity of the IP address. This data can then be used to identify specific malicious activity, such as: the specific script/tool the IP address is using to scan the internet for vulnerable devices, the type/specific vulnerabilities the IP address is scanning for, and even the specific vulnerabilities (and the CVE) it attempted to exploit in the wild.
Search By:
IP Address
GreyNoise Query Language (GNQL)
GreyNoise also has its own custom query syntax, which allows you to search/filter by:
ip - The IP address of the scanning device IP
classification - Whether the device has been categorized as unknown, benign, or malicious
first_seen - The date GreyNoise first observed the device
last_seen - The date GreyNoise most recently observed the device
actor - The benign actor the device has been associated with, such as Shodan, Censys, GoogleBot, etc
tags - A list of the tags the device has been assigned over the past 90 days
spoofable - This IP address has been opportunistically scanning the Internet but has failed to complete a full TCP connection. Any reported activity could be spoofed.
vpn - This IP is associated with a VPN service. Malicious or other activity should not be attributed to the VPN service provider.
vpn_service - The VPN service the IP is associated with
bot - The IP has been associated with known bot activity
metadata.category - Whether the device belongs to a business, ISP, hosting, education, or mobile network
metadata.country OR metadata.source_country - The full name of the country the device is geographically located in
metadata.country_code OR metadata.source_country_code- The two-character country code of the country the device is geographically located in
metadata.destination_country - The full name of the IP scanning destination country
metadata.destination_country_code - The two-character country code of the IP scanning destination country.
single_destintation - A boolean parameter that filters source country IPs that have only been observed in a single destination country. This has to be used in conjunction with destination_country and destination_country_code.
metadata.city - The city the device is geographically located in
metadata.region - The region the device is geographically located in
metadata.organization - The organization that owns the network that the IP address belongs tometadata.rdns - The reverse DNS pointer of the IP
metadata.asn - The autonomous system the IP address belongs to
metadata.tor - Whether or not the device is a known Tor exit node
raw_data.scan.port - The port number(s) the devices has been observed scanning
raw_data.scan.protocol - The protocol of the port the device has been observed scanning
raw_data.web.paths - Any HTTP paths the device has been observed crawling the Internet for
raw_data.web.useragents - Any HTTP user-agents the device has been observed using while crawling the Internet
raw_data.ja3.fingerprint - The JA3 TLS/SSL fingerprint
raw_data.ja3.port - The corresponding TCP port for the given JA3 fingerprint
raw_data.hassh.fingerprint - The HASSH fingerprint
raw_data.hassh.port - The corresponding TCP port for the given HASSH fingerprint
Other Important Details:
GreyNoise produces tags which is the signature-based detection method used to identify actors, tools, and CVEs in their observed activity data. These tags are tracked and using this they can provide insights on the activity of threat actors like:
Trends - GreyNoise classifies a tag as trending when their sensors observe a significant increase in the average number of IPs transmitting traffic within a 10-day period.
Anomalies - GreyNoise classifies a tag as an anomaly when its sensors observe a sudden peak in the number of IPs transmitting traffic within 10 day period.
ODIN
🔗 URL: https://search.odin.io/
🛡️ Defanged: [https://search[.]odin[.]io/]
Summary: ODIN performs internet scanning, including port scanning, host search, vulnerability scanning, and threat assessment.
Cost: Freemium
Data Available:
Host information, including:
Open ports
Vulnerabilities (with associated CVE)
Tags (Anonymous proxy, CDN, Satellite Provider)
Services (Identified via banner responses)
Includes the full raw body of the banner response and extracted information
WhoIS Information
Standard IP Geolocation Information
Exposed Buckets/Files
Buckets are unstructured cloud data storage products that companies often use to host information for their apps, services, websites, etc. These buckets can often contain sensitive files that companies do not realize is open to the internet.
Examples of information commonly stored in buckets:
Attachments/Images sent via instance communication services
Invoices generated by delivery apps or restaurant software
Images/content from an e-commerce website
The bucket files are also indexed and tagged with potential/detected file contents, such as “financial information”.
Search By:
For Host Data
Note: Filters for these search options include:
Search in ASN, Geolocation, or BGP Prefix
Search for exposed ports, services, products, etc.
Access data within a time range for different timestamp fields.
IP address/Host Name
Domain name
Port
Product/Service
CVE
CIDR/IP range
For Exposed Buckets Data
Search based on categories and labels
Search based on the cloud provider
Search based on bucket files
Search with time-based filters
For Exposed Files Data
Search based on the file extension, size, category and label
Search based on bucket and cloud provider
Search with time-based filters
Other Important Details:
No additional information provided.
Cisco Talos Intelligence
🔗 URL: https://talosintelligence.com/
🛡️ Defanged: [https://talosintelligence[.]com/]
Summary: Cisco's dedicated security intelligence platform for threat detection and analysis sources some unique information from Cisco’s telemetry and sensors.
Cost: Freemium
Data Available:
IP, domain, and URL reputation ratings
Email Volume Statistics
Content Category of Email/IP/Domain/URL Activity (e.x. Computers and Internet, Auction, Cryptocurrency, etc)
Search By:
For both Email/Spam Reputation Data and IP/Domain Reputation Data:
IP
URL
Domain
Network Owner
File SHA256
Other Important Details: No additional information provided.
IPInfo
🔗 URL: https://ipinfo.io/
🛡️ Defanged: [https://ipinfo[.]io/]
Summary: Comprehensive IP data provider offering geolocation, anonymization label (VPN, Proxy, TOR, Data Center, etc), ASN info, and more.
Cost: Freemium
Data Available:
Geolocation
ASN information
Anonymization label
Search By:
IP address (IPv4/IPv6)
ASN
Other Important Details: No additional information provided.
Whoxy
🔗 URL: https://www.whoxy.com/
🛡️ Defanged: [https://www[.]whoxy[.]com/]
Summary: WHOIS history and reverse lookup by name or email.
Cost: Freemium
Data Available:
WHOIS records, including domain name and registrar information.
Search By:
Domain name
Owner’s name
Owner’s email address
Company name
Domain keyword.
Other Important Details:
It can be used to identify domains owned by a person by searching via email or name.
Powered by Autowhois.com and Bigdomaindata.com.
Maintains a large historical WHOIS database, reportedly containing records for 345 million domain names.
bgp.he.net
🔗 URL: https://bgp.he.net/
🛡️ Defanged: [https://bgp[.]he[.]net/]
Summary: ASN/IP range lookup by organization name.
Cost: Free
Data Available:
ASN details, including name, number, and peer information.
Search By:
ASN number
IP address
Organization name
Other Important Details:
Beyond ASN lookups, this website provides a wealth of other networking-related tools/information from a map of the global internet backbone (undersea cables, exchanges, etc): https://www.he.net/3d-map/, a global directory of internet exchanges and their exchange participants, extremely powerful and verbose traceroute tools, etc.
Want to access our entire OSINT Knowledge Base when it comes out? You can do so when you become a paid subscriber to the OSINT Insider. Let us do the heavy lifting of cataloguing OSINT tools, resources, and tips for you:
Paid subscribers can also see this entire post, with an additional 40 tools/resources after this point in the post that we couldn’t add to this detailed list because we haven’t finished collecting detailed information about the tools. Want to help build our knowledge base and learn about the other 40+ tools? Come intern for us: https://www.farnsworthintelligence.com/opportunities